Yesterday we hosted a Cybersecurity Awareness Webinar focused on explaining some of the key impacts to SMBs in plain English.
Read MoreTechnology Advisor Blog
Are you still running Windows 7 or Server 2008 in your office? Microsoft will be ending support for Windows 7 and Server 2008 on January 14, 2020. Microsoft made a commitment to provide 10 years of product support for Windows 7 when it was released on October 22, 2009. When this 10-year period ends, Microsoft will discontinue Windows 7 support so that they can focus their investment on supporting newer technologies.
Read MoreTags: Microsoft, cybersecurity
Cybersecurity Awareness Training - Everyone Needs to Get Involved!
Posted by Ann Westerheim on 5/2/19 10:38 AM
Last week, Ekaru hosted a Cybersecurity Awareness Training session at the Cameron Senior Center in Westford, MA. It's part of our mission to raise cybersecurity awareness for EVERYONE.
Read MoreTags: cybersecurity, ransomware
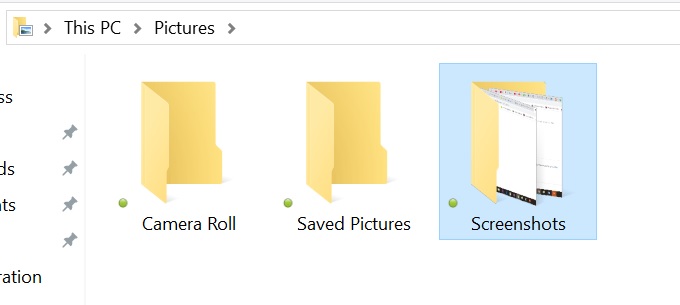
A screenshot is an image of whatever's on your screen. Simply pressing the PrtSc button will save the image of your screen to your clipboard. If you then go into a document or email, you can hit "paste", or Ctrl+V to insert the image. Pretty simple! This is a great short cut when you need to show someone something on your screen or perhaps provide instructions to someone.
Read MoreAre you ready? Microsoft will stop supporting Windows 7 (and Server 2008) in January 2020.
Posted by Ann Westerheim on 2/7/19 10:33 AM
Microsoft will be ending support for Windows 7 and Server 2008 on January 14, 2020. Microsoft made a commitment to provide 10 years of product support for Windows 7 when it was released on October 22, 2009. When this 10-year period ends, Microsoft will discontinue Windows 7 support so that they can focus their investment on supporting newer technologies. This is a standard part of their product life cycle.
Read MoreTags: Windows 7, cybersecurity
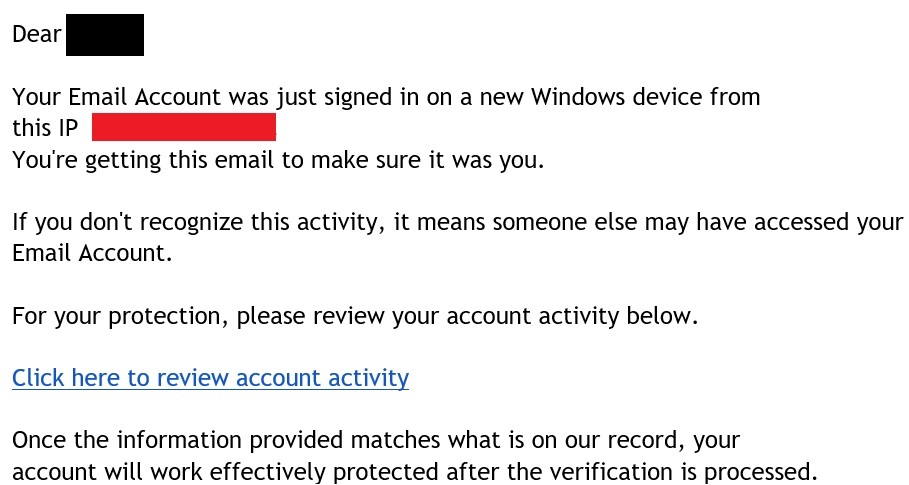
We do a lot of cybersecurity training at Ekaru and one of things we tell people is to "THINK BEFORE YOU CLICK". But what do we need to look out for?
Read MoreTags: email security, cybersecurity
This week an astonishing 773,000,000 records were released in a monster breach. Security researcher Troy Hunt first reported the data set which includes 772,904,991 unique email addresses and over 21 million unique passwords, all recently posted to a hacking forum.
Read MoreTags: password, cybersecurity, Dark Web
Want to achieve your goals in 2019? Get organized and take action!
Posted by Nancy Amato on 1/3/19 10:50 AM
- Before leaving work each day create a To-Do list of your priorities for the next working day. Don’t forget to do this on Fridays. It will help you become more organized.
- As you begin your To-Do list never spend more than 30 minutes being confused. Stop ask for help or - you are wasting time. These are the boundaries you need to set for yourself.
- One benefit of time management is that if you follow your daily list, it will reduce your stress level.
- Set up deadlines on your projects. Put a time limit on your tasks.
- Follow your prioritized list by completing the most critical and demanding tasks first thing in the morning if possible.
- Schedule a break if needed every 90 minutes for a quick glass of water or a cup of coffee. This will help you maintain high productivity throughout the day.
- Exercise and regulating your sleep patterns also helps with time management. Any form of relaxation is important. Exercise is also considered a great stress reliever. Going to bed the same time every night and waking up the same time every day helps with your overall wellbeing. Many presenters have brought this up during the Hubspot Inbound conference.
- Never procrastinate. You know the famous saying ‘Why put off tomorrow what you can do today? Procrastination wastes your time and your company’s time. I recently saw 'Mary Poppins Returns', and Emily Blunt said "Today or Never" - a great motto to live by!
- This one is tricky: Learn how to multitask! When working in a fast paced environment it’s the only way to survive some days. This is not easy and may take lots of practice!
- Start each day by being on time at work. Everyone has traffic to deal with and family morning rituals, but always give yourself extra time to get to work. If you start your day late everyday then you should stay later to make up your time so why start off late everyday…It’s a waste of your time!
Read More
Tags: SMB, Time Management
Cyber Attacks Increasing - Cape Cod Community College Hacked for $800,000
Posted by Ann Westerheim on 12/12/18 12:01 PM
Cyber threats are real and they're local. Major corporations like Marriott make the big headlines, but too many smaller businesses and institutions think they're "under the radar". Attacks are widespread and they're automated. The average firewall is getting hundreds of thousands of intrusion attempts per month, over 50 ransomware attempts, and twelve phishing attempts. All it takes is ONE user clicking on ONE wrong link and a lot of damage can be done.
Read MoreTags: cybersecurity, SMB, ransomware
.png)