In Ekaru’s previous blog, we went over how typos can unexpectedly lead you to mimicked websites designed by hackers to steal your personal information. But what if I told you that on top of having to be hyper vigilant of spelling, you also need to check a URL’s characters if all letters are from the same font?
Tricks hackers use to scam unsuspecting individuals usually consist of spam texts, phishing emails impersonating reputable companies, scams claiming you owe a specific amount of money, creating a sense of urgency - all are attempts to fatigue you and steal your information. For some, these tricks have become easy to spot due to recognizing the signs from their intensive cybersecurity awareness training. However, bad actors use evolving technology and strategies to improve their game and become harder and harder to detect.
One of their strategies to become harder to detect, is the usage of visuals in random letters from different fonts. This is a term we call Internalized Domain Name (IDN) Homograph attack.
Technology Advisor Blog
Tags: phishing, Monitoring, technology, small business technology, small business technology advice., Cybersecurity, email scams, cybersecurity, DNS Protection, Homograph Attack
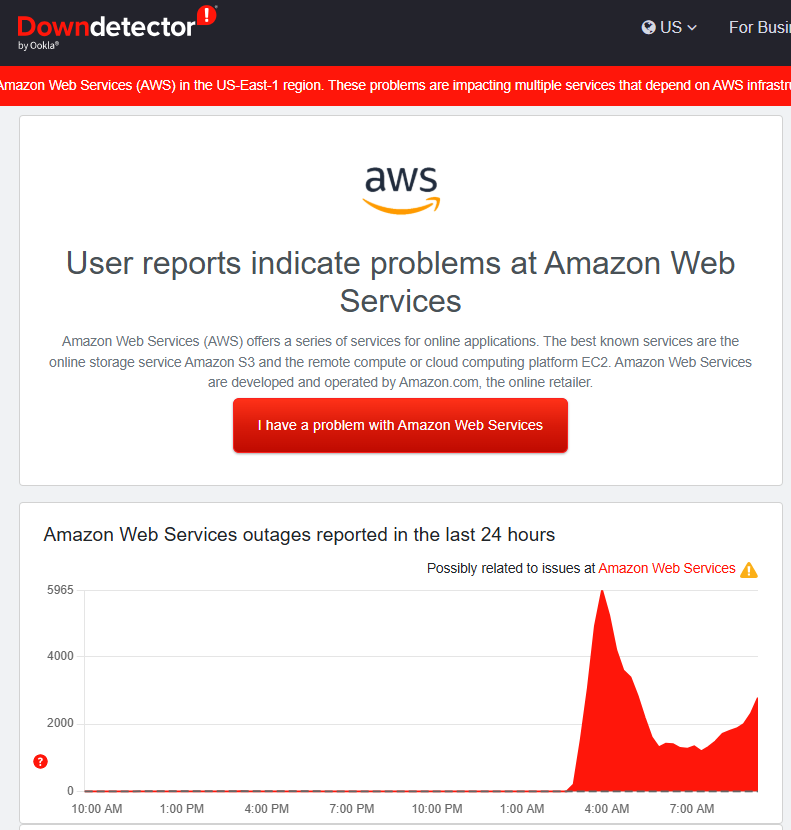
It’s Raining in Boston - and in the Cloud: What Today’s AWS Outage Teaches Us
Posted by Ann Westerheim on 10/20/25 12:09 PM
If your favorite app wouldn’t load this morning, you weren’t alone. Amazon Web Services (AWS) - the cloud backbone behind a huge slice of the internet - had a major hiccup in its US-EAST-1 (Northern Virginia) region in the early hours today. Reports began around ~3:00 a.m. ET, with recovery signs a couple hours later. By mid-morning, Amazon said the underlying issue had been fully mitigated. Still, the ripple effects were hard to miss: services like Snapchat, Zoom, Signal, Fortnite, Coinbase/Robinhood, Perplexity, and even airline sites such as Delta and United saw issues at points during the incident. DownDetector tallied millions of outage reports across the globe. The Verge
Read MoreTags: small business, technology, cloud
Networks are The Powerhouse of a Business, They Must Be Protected
Posted by Sarah Carroll on 10/17/25 11:28 AM
When keeping business operations alive, security is essential. Security isn’t just strong passwords of 16 or more characters across multiple different websites/accounts, or MFA, it’s a deeper-rooted step to take with your networks to prevent most cybersecurity threats.
From a 2021 Verizon study, “61% of small to mid-size businesses experienced a cyberattack in 2021”. In 2023 73% of small businesses faced cyber-attacks. In 2024, 94% of small to medium sized businesses faced a cybersecurity attack. The number keeps increasing each year with small businesses affected. Something must be done to protect businesses from such cyber attacks.
The mindset has probably come up multiple times in conversation; “I’m a small business, I’m too small to be known for hackers to try and target me”. It’s not exactly if it happens, it all matters as to when. Don’t wait until that ‘when’ turns into ‘today’ when you receive a socially engineered scam that looks legit. Scams are becoming harder to identify, when you are not investing in proper cybersecurity measures, the wrong people will notice you do not have the tools or budget.
Tags: security protection, support, technology, network security, malware, security awareness training, online safety, Cybersecurity Awareness Training
Got Electronics? Join Us For Ekaru's Quarterly Electronics Recycling Event!
Posted by Sarah Carroll on 9/18/25 4:45 PM
Aside from Ekaru’s qualified team providing IT solutions and cybersecurity awareness training, we enjoy giving back to our community.
When you purchase a new device such as a laptop, monitor, or a new smartphone, the first step is transferring all your essential data to the new device. Once you’ve transferred all the essentials, you’re left with your former device, inactive and collecting dust on the shelf.
Understanding the materials that create these tools we use in our everyday lives, it’s evident that you cannot just discard these devices in normal everyday trash bins.
Does this resonate that you recently got that new iPhone, MacBook or monitors? That’s where we come in! Our team at Ekaru hosts quarterly electronics recycling events supported by eWaste.
Read MoreTags: computer security, computer, technology, Security Requirements, productivity, small business technology advice., cybersecurity, data security, cybersecurity training, electronics recycling, Cybersecurity, Social Media
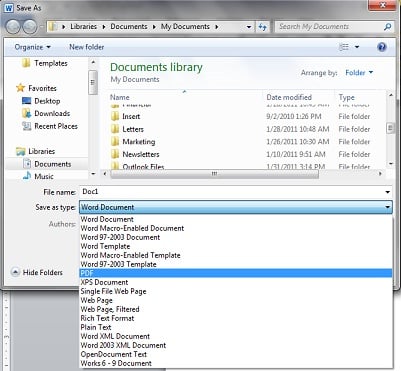
Here's a tip to get more from the small business technology you already have. One of the helpful features in Office 2010 is the ability to directly create a PDF document by using the "save as PDF" feature. Instead of relying on a third-party application, the capability is built right in.
Tags: PDF, small business, Microsoft Office, technology
.png)