Amazon provides users with an extensive ecommerce platform, with purchases ranging from clothing, games, kitchen, niche topics, home décor, technology, and more right at your fingertips. Exceptional delivery time on everyday items, insightful reviews, and a great return policy. Though Amazon has millions of official and 3rd party sellers using its ecommerce platform in showcasing their products & services, there are risks to be aware of especially when buying laptops.
In recent months, we have heard reports of users buying computers from Amazon with complicated issues regarding unclear support policy plans and overall, not what they were expecting. In today’s blog post, we are going to discuss key risks that come with purchasing from 3rd party sellers on Amazon, with misleading specs and even receiving used items.
At Ekaru, our goal isn’t to instill fear but provide users with the most up-to-date cybersecurity findings to help you make informed decisions. Especially when it comes to your devices and overall cybersecurity hygiene. Located in Westford MA, we work alongside multiple small and medium-sized businesses in the Boston metropolitan area ranging from doctor offices, construction, attorney offices, accounting, and so much more.
Technology Advisor Blog
Before You Buy on Amazon: Consider the Official Computer Website First
Posted by Sarah Carroll on 2/25/26 2:23 PM
Tags: laptop, small business, RAM, small business technology advice., specifications, cybersecurity
You did it. You upgraded to that big, beautiful, high-resolution monitor. Maybe it’s 27 inches. Maybe it’s 4K. Maybe it looked absolutely stunning in the store.
Read MoreTags: productivity, Computer Settings, High resolution display, Display settings
By the end of January, you likely have received your tax return documents with a deadline completion set for April 15, 2026.
With the current time frame of 8-10 weeks to completion, some will leave their taxes to the last minute or engage an accountant for their services. What if we told you that the longer you wait to do your taxes, the more at risk your information falls into the hands of a hacker? In turn causing the big headache that goes along with identity theft and tax fraud.
Hackers have found intricate loopholes to steal your personal and tax information for malicious and financial gain. At Ekaru, our goal isn’t to instill fear when it comes to cybersecurity threats. It’s essential to understand that anyone can become an unsuspecting victim of a scam. Our intent is to provide you and your business with the essential tools to defend your personal data with peace of mind. In today’s blog, we will discuss why it’s better to get your taxes done proactively.
Tags: Cybersecurity, email scams, cybersecurity, TaxScam, Fraud
In January, multiple updates for Windows 11 affected millions of users. These mostly consisted of security patches, bug fixes, AI implementation and a new feature in the mix to improve the user experience for Microsoft users. As we enter a new month, Microsoft has another wave of updates for users that can help improve their security posture, enhance some features and discontinued others.
Read MoreTags: Microsoft Windows Update, Wi-Fi, cybersecurity, AI, Windows11
Jan 2026: ATM Skimmers, Social Media Phishing & Windows 11 Recap
Posted by Sarah Carroll on 1/29/26 3:41 PM
Just because it is January, does not mean hackers are ceasing their cyber attacks on businesses and unsuspecting victims. This month, we have noticed scams such as stealing debit card information at local stores hitting close to home, sophisticated phishing attempts across social media accounts, particularly Instagram, and Windows 11 updates we’ve observed for users. At Ekaru, our goals are to provide users with the most up-to-date news for cybersecurity locally and across the US, while also providing tips to keeping you and businesses safe.
Read MoreTags: password, cybersecurity, Cybersecurity, Social Media, Windows11, ATMScam
Shutdown vs. Restart: What’s the Difference and Why It Matters for Your Business
Posted by Sarah Carroll on 1/23/26 12:38 PM
Have you been in the middle of a significant deadline with complete focus, then all a sudden your desktop shuts down abruptly causing your focus and productivity to cease? It happens to the best of us.
Read MoreTags: Slow Computer, computer security, cybersecurity, Computer Tip, Computer Shutdown, Computer Restart
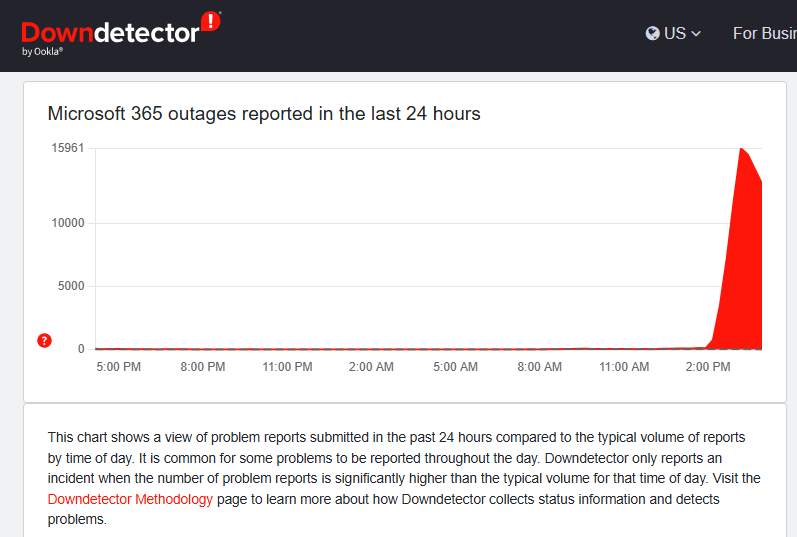
Microsoft 365 Outage Today: What's going on and why it matters
Posted by Ann Westerheim on 1/22/26 4:24 PM
Tags: Microsoft, Internet Outage, Microsoft 365
Why Rebooting Your Computer Is One of the Easiest Security Wins
Posted by Ann Westerheim on 1/21/26 5:42 PM
Security updates aren’t the most exciting topic—but they are one of the most important parts of keeping your business protected.
Right now, we’re seeing something that surprises a lot of people: about 13% of the systems in our community need a reboot. That means critical security updates are downloaded… but not fully protecting those computers yet.
Why reboots matter more than most people realize
Each month, Microsoft releases security fixes (often called “Patch Tuesday”). Behind the scenes, we carefully test critical patches within 24 hours, then roll out additional updates over the following week. This testing and deployment process is a core part of a healthy security program.
Here’s the catch: many of those security patches don’t actually take effect until you reboot. And we're seeing too many computers in our community that haven't been rebooted in too long.
Even more important, some patches are sequential. If the first update doesn’t fully install because the
Read MoreTags: Microsoft Security Patches, Patch Policy, cybersecurity
Before You Prove You’re Human, Make Sure You’re Not Helping Hackers
Posted by Ann Westerheim on 1/16/26 4:18 PM
Most of us barely notice CAPTCHA checks anymore.
You know the ones - the little box that says “I am not a robot”, or the quick image puzzle before you can move on. The little puzzle may ask you to select the images that contain traffic lights, bicycles, or crosswalks. We see them so often that clicking through has become second nature. In fact, many people associate CAPTCHAs with extra security, not risk.
Read MoreTags: cybersecurity, Cybersecurity Awareness Training
But wait - there's more! While we had a blog discussing Windows shortcuts to boost your productivity throughout the week, we also want to inform you of what’s to come for January 2026 updates regarding Windows 11. To provide an understanding of what’s coming your way, what you can expect for patch security updates, AI powered Copilot, PC features to devices, and more. Our intentions here at Ekaru are to provide our clients, and those searching for their next MSP, with the most up-to-date knowledge on all things cybersecurity and windows applications to ensure you are proactive and aware in the world of cybersecurity.
Read MoreTags: Security, Microsoft, Monitoring, cybersecurity, Windows11
.png)