Aside from Ekaru’s qualified team providing IT solutions and cybersecurity awareness training, we enjoy giving back to our community.
When you purchase a new device such as a laptop, monitor, or a new smartphone, the first step is transferring all your essential data to the new device. Once you’ve transferred all the essentials, you’re left with your former device, inactive and collecting dust on the shelf.
Understanding the materials that create these tools we use in our everyday lives, it’s evident that you cannot just discard these devices in normal everyday trash bins.
Does this resonate that you recently got that new iPhone, MacBook or monitors? That’s where we come in! Our team at Ekaru hosts quarterly electronics recycling events supported by eWaste.
Read More
Tags:
computer security,
computer,
technology,
Security Requirements,
productivity,
small business technology advice.,
cybersecurity,
data security,
cybersecurity training,
electronics recycling,
Cybersecurity, Social Media
Penetration testing (or pen testing for short) is a proactive way to protect your business from cyberattacks. It simulates real-world attacks to identify vulnerabilities before cybercriminals can exploit them. For small businesses, often working with limited security resources, pen testing is a critical tool to uncover hidden risks, meet compliance requirements, and strengthen defenses.
Your business data and customer information need strong protection to maintain trust and meet compliance standards. Modern automated tools make professional security testing both accessible and cost-effective for smaller companies. Through regular testing, you can build a clear roadmap to strengthen your defenses and stay ahead of emerging threats.
Read More
Tags:
security protection,
business continuity,
cybersecurity,
data security,
cybersecurity training,
pen test,
Penetration Testing
Have you ever been hooked to a phishing attempt? Did you know that phishing is involved in 70% of breaches? Whether it’s an email, phone call, or text message, these are some of the common ways bad actors use to obtain your personal and financial information for malicious gain. Phishing emails were introduced into our lives decade(s) ago and have grown increasingly creative and sophisticated with native language use and perfect grammar.
Read More
Tags:
small business,
phishing,
Cybersecurity, email scams,
cybersecurity, ransomware,
data security,
spoofing,
Security Awareness,
email spoofing
Every year, Verizon publishes a Data Breach Investigation Report (DBIR). The Verizon DBIR is one of the most comprehensive reports illustrating REAL security incidents and breaches, not just hypothetical "this could happen" warnings. The 2025 Report - the 18th annual report! - was published on April 23, 2025 and as usual, its full of inciteful information for both small business AND enterprise. To generate the report, the Verizon DBIR team analyzed 22,053 real-world security incidents, of which 12,195 were confirmed data breaches.
Read More
Tags:
small business technology advice.,
cybersecurity, ransomware,
cybersecurity,
data security,
incident response,
SecurityBreach

With the start of the new month and Tax season now over, cybercriminals are beginning to shift their focus on to new trends. This time targeting tech and healthcare giants for patient sensitive information out by the millions.
I’m sure you all have heard it before ‘I’m just one person and keep my circle small, I’m not going to fall victim to a cybercrime. I’m so careful.’ Or even; “I just use the necessities and take what I believe are the cautionary steps”. Until you’re not. Even just this morning a colleague received a phishing text claiming they saw their ‘resume’ and had a job opening with no further context. They pointed out the message’s red flags, which included a high amount of compensation for said job, no description of position or company name and contact information did not match. As annoying as it is to receive these types of unwanted messages, the attempt likely came from the individual placing their email to receive newsletters & updates of a product and service of their choosing. Not expecting their email or any other additional information to be involved for phishing attempts.
Read More
Tags:
computer security,
small business technology advice.,
cybersecurity, ransomware,
cybersecurity,
data security,
incident response
Building on annual success Cybersecurity Awareness Month 2022 is set to highlight the growing importance of cybersecurity in our daily lives and look to empower everyday individuals and business to take cybersecurity steps by making cyber more accessible.
Read More
Tags:
small business,
small business technology,
cybersecurity,
data security
Cyber criminals can use data leaked in big breaches to cause more harm to you with phishing emails. Data from big breaches, which have almost become commonplace, wind up on the Dark Web quite quickly. After they have your info via the Dark Web, they can craft some very convincing emails to you. They can use identifiable information to customize the email to make it look legit.
Read More
Tags:
e-Mail,
cybersecurity,
data security
Companies across industries are experiencing unprecedented stress and pressure right now on account of the COVID-19 pandemic. Offices are shutting down, employees are working remotely, and the sense of structure your team was accustomed to may be starting to feel like a distant memory.
Read More
Tags:
data backup,
cloud,
data security,
remote work
Microsoft Windows 7 has long been a favorite operating system for business, but now the end of life for support is just one year away. Although we're still seeing some line of business applications with problems running on Windows 10, it would be ill-advised to roll out any new systems with this operating system. The official end date for extended support is January 14, 2020. After this time, there will be no more security updates, and any system would be at risk for security problems, and out of compliance for a long list of industry security requirements.
Read More
Tags:
Microsoft Windows 7,
data security
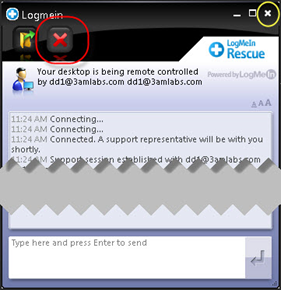
The "tech support" scam is a common threat on the Internet. While working on your computer, a pop up will appear that says your computer has a problem and help is just a phone call or click away. Many of these scams pretend to be from Microsoft. The graphics may look very professional, and the tech jargon sounds convincing enough that may people fall for these scams. After the "repair" is done, then you'll be asked for a credit card to pay. Most people assume they won't fall for a scam, but if you're very busy, and the support price is low enough, it could seem like the fastest and most efficient way to get support and get back to work.
Read More
Tags:
cybersecurity,
data security
.png)