If your email isn’t working today, you’re not alone.
Read MoreTechnology Advisor Blog
Ann Westerheim
Recent Posts
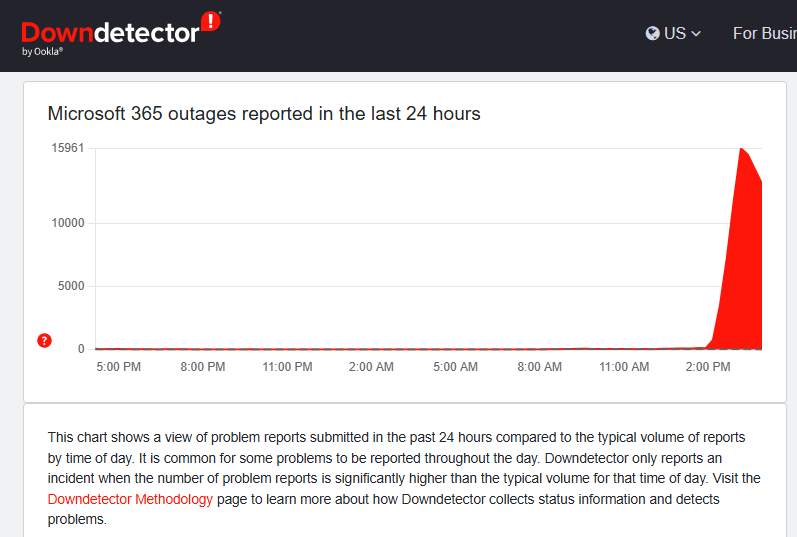
Microsoft 365 Outage Today: What's going on and why it matters
Posted by Ann Westerheim on 1/22/26 4:24 PM
Tags: Microsoft, Internet Outage, Microsoft 365
Why Rebooting Your Computer Is One of the Easiest Security Wins
Posted by Ann Westerheim on 1/21/26 5:42 PM
Security updates aren’t the most exciting topic—but they are one of the most important parts of keeping your business protected.
Right now, we’re seeing something that surprises a lot of people: about 13% of the systems in our community need a reboot. That means critical security updates are downloaded… but not fully protecting those computers yet.
Why reboots matter more than most people realize
Each month, Microsoft releases security fixes (often called “Patch Tuesday”). Behind the scenes, we carefully test critical patches within 24 hours, then roll out additional updates over the following week. This testing and deployment process is a core part of a healthy security program.
Here’s the catch: many of those security patches don’t actually take effect until you reboot. And we're seeing too many computers in our community that haven't been rebooted in too long.
Even more important, some patches are sequential. If the first update doesn’t fully install because the
Read MoreTags: Microsoft Security Patches, Patch Policy, cybersecurity
Before You Prove You’re Human, Make Sure You’re Not Helping Hackers
Posted by Ann Westerheim on 1/16/26 4:18 PM
Most of us barely notice CAPTCHA checks anymore.
You know the ones - the little box that says “I am not a robot”, or the quick image puzzle before you can move on. The little puzzle may ask you to select the images that contain traffic lights, bicycles, or crosswalks. We see them so often that clicking through has become second nature. In fact, many people associate CAPTCHAs with extra security, not risk.
Read MoreTags: cybersecurity, Cybersecurity Awareness Training
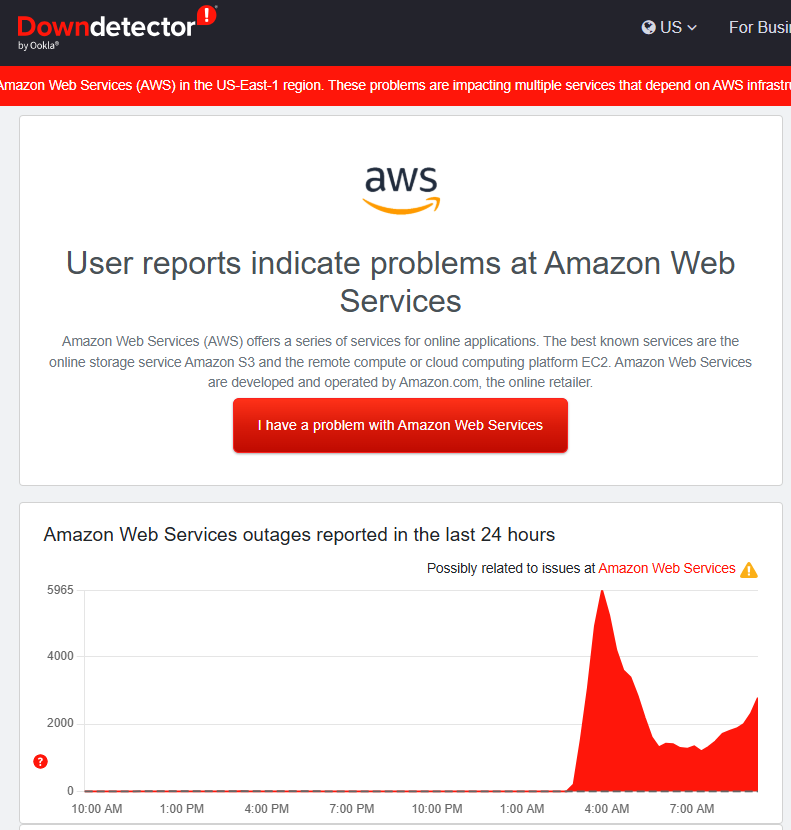
It’s Raining in Boston - and in the Cloud: What Today’s AWS Outage Teaches Us
Posted by Ann Westerheim on 10/20/25 12:09 PM
If your favorite app wouldn’t load this morning, you weren’t alone. Amazon Web Services (AWS) - the cloud backbone behind a huge slice of the internet - had a major hiccup in its US-EAST-1 (Northern Virginia) region in the early hours today. Reports began around ~3:00 a.m. ET, with recovery signs a couple hours later. By mid-morning, Amazon said the underlying issue had been fully mitigated. Still, the ripple effects were hard to miss: services like Snapchat, Zoom, Signal, Fortnite, Coinbase/Robinhood, Perplexity, and even airline sites such as Delta and United saw issues at points during the incident. DownDetector tallied millions of outage reports across the globe. The Verge
Read MoreTags: small business, technology, cloud
What Really Happens When Your Email Gets Hacked (And How to Stop It)
Posted by Ann Westerheim on 10/17/25 4:08 PM
This week, we received what looked like an official Request for Proposal (RFP) email from a local business we know. It was well-written, professional, and completely believable.
Read MoreTags: eMail, cybersecurity, hack
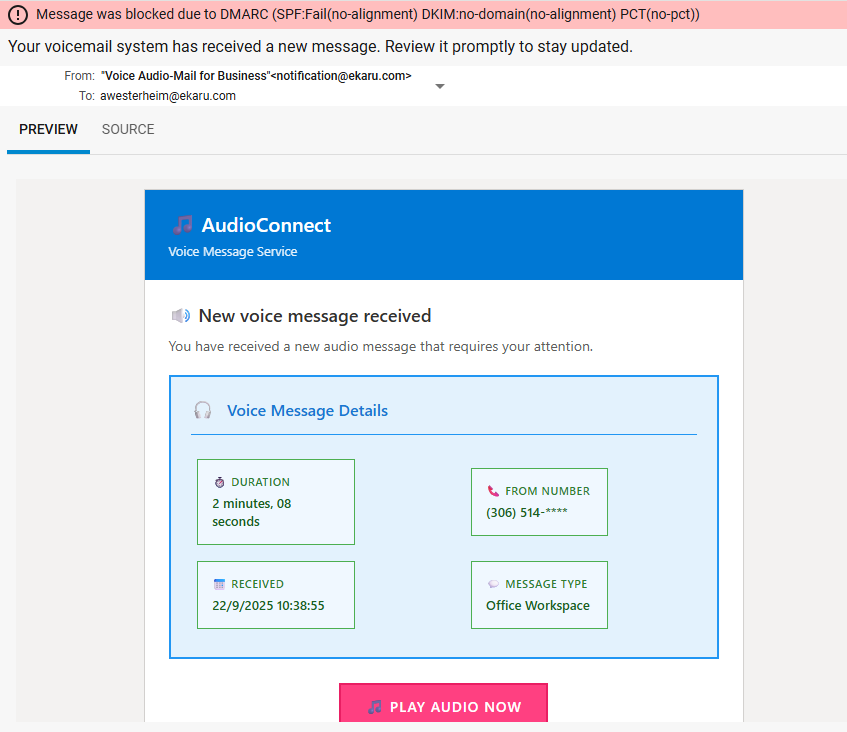
Why DMARC Matters: A Real-Life Voicemail Scam Example Every Business Should See
Posted by Ann Westerheim on 9/22/25 12:44 PM
Last week, I didn’t even see a suspicious voicemail notification in my inbox - and that’s the point! Our email security blocked it before it ever got to me. At first glance, the message looked pretty legitimate. It was well-formatted, had a sense of urgency - “Your voicemail system has received a new message. Review it promptly to stay updated”, and looked like something that could easily trick someone into clicking.
Read MoreTags: eMail, cybersecurity, DMARC, Cybersecurity Awareness Training
Goodbye Windows 10, Hello Windows 11: What Local Businesses Need to Know Before October 14, 2025
Posted by Ann Westerheim on 9/12/25 12:51 PM
Microsoft has officially announced that Windows 10 support will end on October 14, 2025. After that date, no more free security updates will be released. For small businesses, this isn’t just a technical detail - it’s a security and business risk. Cybercriminals often target outdated systems, and without regular patches, Windows 10 devices will quickly become vulnerable.
Read MoreTags: Microsoft, cybersecurity, windows 10
Ekaru Achieves Generative AI Certification from Breach Secure Now to Lead Clients in Secure, Strategic AI Adoption
Posted by Ann Westerheim on 9/3/25 6:18 PM
Ekaru, a trusted provider of managed IT and cybersecurity services, is proud to announce that we are now Generative AI Certified by Breach Secure Now (BSN). BSN is a leading provider of human-centric cybersecurity, AI awareness, and productivity training. This industry-first certification empowers our team to confidently lead clients through the complexities of AI adoption - safely, strategically, and securely.
Read MoreTags: small business technology, cybersecurity, AI
From Risk to Readiness: Why GRC Matters for Every Small Business
Posted by Ann Westerheim on 8/21/25 3:35 PM
A Real-World Wake-Up Call
Last week a 10-person machine shop in the Boston area reached out to us with an urgent challenge. They were eager to win Department of Defense contracts, but there was one major roadblock: compliance. Specifically, they needed to meet CMMC (Cybersecurity Maturity Model Certification) standards to even qualify.
Read MoreTags: small business technology, cybersecurity, GRC
Ransomware attacks can destroy a business in hours, yet having a local incident response team alongside national experts provides direct support when every minute counts. A nearby team delivers immediate on-site assistance, translates complex technical information, and works directly with your staff while national teams handle remote tasks. When a local business was recently locked out of all their systems after a ransomware attack, a nationally recognized incident response team needed "boots on the ground" and we were honored to be called to help.
Read MoreTags: cybersecurity, ransomware, Cyber Insurance, ransomware recovery
.png)