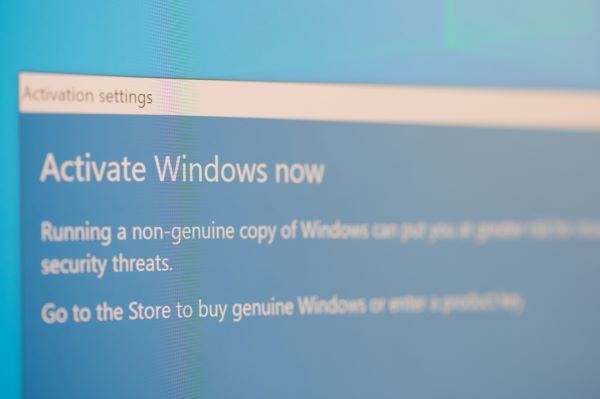
Starting May 5, 2025, all businesses - regardless of size - must meet Microsoft’s stricter email authentication requirements when sending to Outlook, Hotmail, and Live addresses. These changes are designed to reduce spoofing and impersonation, aligning with similar updates from Google and Yahoo to improve overall email security.
Read MoreTechnology Advisor Blog
DMARC Gets Serious: Microsoft Enforces Stricter Email Rules
Posted by Ann Westerheim on 4/30/25 4:47 PM
Tags: eMail, SPF record, Cybersecurity, email scams, cybersecurity, DMARC
Spring Cleaning for your Cybersecurity: 10 Things You're Probably Overlooking
Posted by Ann Westerheim on 4/29/25 4:25 PM
Just like your home needs a good spring cleaning, your technology and data need regular organization too. Cybersecurity best practices act like a home organization system for your digital life - keeping your accounts, passwords, and access permissions tidy, updated, and secure. This guide will show you proven methods in protecting your information while making sure your systems run smoothly using smart organization techniques. Learning the straightforward steps to defend yourself against current threats and build a more secure foundation for your business and personal data. Cleaning out your closets this Spring? Make sure you take care of your digital clutter as well!
Read MoreTags: computer security, strong passwords, security protection, Cleaning your computer, data backup, cybersecurity, Privacy, cybersecurity training, General
Cybercrime Soaring in the 2020s - Businesses and People at Risk
Posted by Sarah Carroll on 4/25/25 12:35 PM
With the development of generative AI becoming more sophisticated for both positive and malicious intent, it’s no surprise there has been an increased surge of cybercrime happening all around the world.
In 2024 alone, we can see these reflect in the 33% increased losses in the US compared to the previous year 2023. According to the FBI Internet Crime Complaint Center (IC3), losses from cybercrime in 2024 exceeded $16 billion, with the top three causes of financial loss stemming from phishing, extortion, and personal data breaches. Important note: When it comes to data incidents, the difference in context is that data incidents are suspicious activity occurring across accounts. A data breach refers to the confirmation of systems being given unauthorized access with malicious intent with financial loss.
Tags: phishing, Cybersecurity, email scams, cybersecurity, Artificial Intelligence
Do small businesses need cybersecurity? YES! Data shows that half of all cyber attacks target small organizations, making them prime targets alongside large corporations. Major security breaches at Fortune 500 companies grab headlines, yet local businesses, nonprofits, and municipalities face ongoing threats that can expose donor databases, financial records, and private customer details. Each year, Verizon publishes the Data Breach Investigations Report which is loaded with statistics on the latest updates on real-world breaches. Reports like this make it clear: small businesses aren't flying under the radar - they're in the crosshairs. Understanding real-world breach data helps you prepare, protect and stay resilient.
Read MoreTags: small business, cybersecurity, incident response
Did you know that in October, Microsoft will no longer be operating on Windows 10? Or that Microsoft is disabling ActiveX controls within the month of May? Are you aware that Microsoft’s April security updates intentionally added a folder that you must NOT delete? As a small business utilizing all your team’s energy and resources, it can be overwhelming keeping up with the multiple security updates ensuring your business’ safety.
Read MoreTags: Microsoft Updates, cybersecurity
Keyboard Shortcuts – These are a few of my favorite things!
Keyboard shortcuts are one of the simplest ways to boost your productivity - yet they're often overlooked. These quick key combinations help you navigate, format, and multitask faster without ever taking your hands off the keyboard. Whether you're writing emails, managing files, or working in Microsoft 365, learning a few key shortcuts can save minutes every day and hours over time. It’s a small change with a big payoff!
Read MoreTags: small business technology advice., cybersecurity, Computer Tip
Credit Card Fraud Is a Headache and Business Cybercrime Is a Full-Blown Crisis
Posted by Sarah Carroll on 4/11/25 9:10 AM
Did you know that 28% of consumers have fallen victim to credit card fraud in the last year? With nearly a third of people affected, it’s no surprise that 37% report feeling anxious about their credit card accounts being compromised. Families and career-driven individuals are especially on edge, with Gen X and Millennials (40%) sharing equally high levels of concern.
Read MoreTags: phishing, small business technology advice., cybersecurity, ransomware, cybersecurity, Fraud
If You've Never Thought of Cybersecurity, You're Exactly Who The Cyber Criminals Want
Posted by Ann Westerheim on 4/9/25 9:26 AM
Cybersecurity and AI have become inseparable forces that create immediate risks to local businesses, regardless of size. Small organizations are now prime targets for criminals who use artificial intelligence to automate attacks, making every business vulnerable.
Major corporate breaches grab headlines, yet the silent wave of cyber attacks on local companies goes unreported, leaving many business owners with a dangerous false sense of safety. Your organization needs basic protective steps that could prevent most attacks, along with cost-effective solutions to shield your business from financial losses and reputation damage. The stakes are high - companies that fall victim to these attacks often struggle to keep their doors open.
Read MoreTags: small business technology advice., Cybersecurity, email scams, cybersecurity training
Understanding Quit Claim Deed Fraud: FBI Boston Steps In as Scams Escalate
Posted by Sarah Carroll on 4/4/25 12:28 PM
Happy April and Spring to all! We have made it through another New England winter. The April showers will eventually bring us May flowers.
For the month of April, Tax Scams are on the rise across the US. Locally, a more sinister scam is on the rise, leaving hundreds of folks devastated financially in its wake. The FBI has issued a warning urging property owners and Real estate agents of Quit Claim Deed fraud (home theft) to avoid losing their property right from under them.
Tags: cybersecurity, cybersecurity training, online safety
Why Delaying a Written Information Security Plan (WISP) Could Be Your Business's Costliest Mistake
Posted by Ann Westerheim on 4/1/25 4:03 PM
A Written Information Security Plan (WISP)acts as your small business's shield against cyber threats, protecting both your data and financial health. Research shows 43% of cyber attacks target small businesses directly, making clear protocols and response strategies a must-have for your operations. Verizon 2024 Data Breach Investigations Report
Tags: service, disaster recovery, small business technology advice., cybersecurity, security risk assessment, ransomware recovery, SecurityBreach
.png)