Coordinating a Wishlist for the holidays with your friends, family and loved ones can be challenging. Especially when no two people are the same. In a lot of cases, whether you utilize your time management right during the season or not, (it’s completely understandable if you don’t, it’s a stressful time in the work-life balance realm), sometimes the best gift, when you don’t know what to get, is a gift card.
Read MoreTechnology Advisor Blog
Gift Cards-An Easy Gift Solution but Proceed with Caution
Posted by Sarah Carroll on 11/13/25 10:40 AM
Tags: phishing, email security, lifecycle, cybersecurity, Fraud, Cybersecurity Awareness Training, Gift Card Scams
Tags: email security, cybersecurity, security awareness training
We do a lot of cybersecurity training at Ekaru and one of things we tell people is to "THINK BEFORE YOU CLICK". But what do we need to look out for?
Read MoreTags: email security, cybersecurity
Sending an email to more than just a few recipients? DON'T hit the send key before reading this....
Posted by Ann Westerheim on 4/16/18 3:54 PM
You need to send an important update or invitation to all your clients and you're ready to hit the "send" key. Don't!
Read MoreTags: eMail, email security
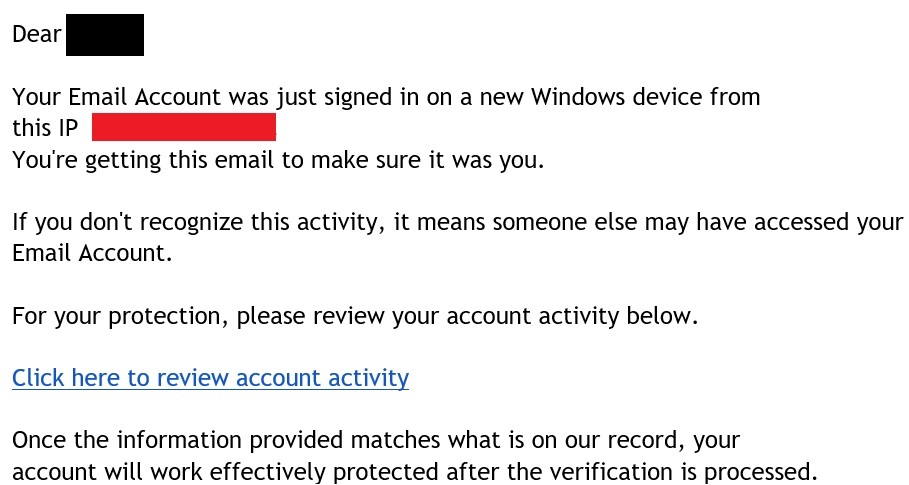
Beware of Phishing attempt to "Authenticate your Account"
Posted by Ann Westerheim on 7/25/17 9:12 AM
Stay alert when reading through your email. Our Cybersecurity advice focuses on "layers" of security, and even with all the technology in place to protect you, the "bad actors" will always resort to new tricks. End user education and vigilance are key.
Read MoreTags: phishing, email security, cybersecurity
One of the services we provide to our clients is spam filtering. The goal is to stop the spam BEFORE it gets to the mail server so it doesn't wind up on the users' desktop, laptop, iPad, smart phone, etc.... Each month when we do the reporting and roll up the numbers, it's amazing how much volume there is. Overall, around 80% of all email traffic is flagged as spam. For some of our clients, this means blocking out tens of thousands of messages a month. I looked at our own domain yesterday, and in February, over 10,000 messages were blocked or quarantined, including 348 emails containing viruses.
Tags: eMail, spam filtering, email security, spam
This is the time of year when many people travel. We have received a lot of questions recently about the latest email security threat: a new wave of "phishing" emails that are based on flight information notifications.
Tags: phishing, email security
Although email typically has a layer of security protection in the form of a password, users need to be aware that emails sent "in the clear" (not encrypted), CAN be intercepted and read by other parties using available tools.
Tags: email security, Encryption
.png)