Technology fuels local businesses these days, helping them achieve their goals and vision. At the same time, local businesses are also at increased risk for growing cyber threats worldwide – ALL businesses are impacted, not just the big ones that make national news. One of the important foundations of keeping your technology safe is to conduct a security risk assessment each year (at least!).
Read MoreTechnology Advisor Blog
Technology New Year's Resolution: Prioritize Your Technology Gaps
Posted by Ann Westerheim on 12/28/21 3:34 PM
Tags: small business, cybersecurity, cybersecurity training, security risk assessment
Cybersecurity headlines may sound scary, but it’s important for local businesses to know there are a lot of smart and affordable things you can do to fight back to stay more secure online and increase your chances of surviving a cyber event. A basic security risk assessment can help identify security gaps to remediate, and ongoing employee training will greatly help reduce “clicks” on the wrong things. Preventing problems is a lot less expensive and more effective than responding to an incident, but it’s not possible to eliminate all risk. As a technology service provider, Ekaru has been working with local businesses in the greater Boston area for many years, and having an incident response (IR) plan will make a big difference in your ability to successfully recover after a cyber incident.
Read MoreTags: cybersecurity, cybersecurity training, incident response plan
Don't Get Scammed by a Turkey
It’s Thanksgiving week and that also means that the holiday season has officially started! And just like the holiday season of our youth, this is the time of year when we as adults tend to get caught up in the excitement and the fun of the times, and let our guard down.
Read MoreTags: cybersecurity
Tags: email security, cybersecurity, security awareness training
CMMC - Cybersecurity Maturity Model Certification - has been a much-discussed topic in cybersecurity this year. Theft of intellectual property and sensitive information from all industrial sectors as a result of malicious cyber activity threatens economic security and national security.
Read MoreTags: small business, cybersecurity, CMMC
October is time for Halloween, Pumpkin Spiced Lattes, and Cybersecurity Awareness Month! Have you ever wondered why there are so many quirky holidays? National Talk Like Shakespeare Day is celebrated on April 23rd for example. There's also Squirrel Appreciation Day which is on January 21st. It may seem confusing, but this just goes to show how diverse our culture really is! While it may seem like some of these holidays are a bit silly, one of them is pretty important: an entire month dedicated to cybersecurity. Now that’s a topic worthy of a holiday!
Read MoreTags: cybersecurity, cybersecurity training
Ekaru Announces Commitment to Global Efforts Advocating for Cybersecurity and Online Behavior Change during Cybersecurity Awareness Month
Posted by Ann Westerheim on 9/27/21 4:01 PM
This year’s initiative highlights the growing importance of cybersecurity and encouraging individuals and organizations to take necessary measures to stay safe and secure in an increasingly connected world.
Read MoreTags: cybersecurity, cybersecurity training
Cybersecurity: 4 Ways Your Employees Could Be Putting You at Risk
Posted by Ann Westerheim on 9/13/21 5:27 PM
Did you know that the global cost of cyber crimes will go over $2 trillion by 2021? It’s also just not government agencies or large corporations that have to worry about cyber attacks and data breaches. Small businesses are actually the biggest target for cyber criminals because they often have smaller IT teams and less security.
Read MoreTags: cybersecurity, cybersecurity training
Back to School: How to Get Started with an Employee Cybersecurity Training Program
Posted by Ann Westerheim on 9/8/21 4:38 PM
September is time for back to school and back to business! This is a great time to get serious about training your employees to understand their role in helping a business or organization stay safe.
Read MoreTags: cybersecurity, ransomware, cybersecurity training
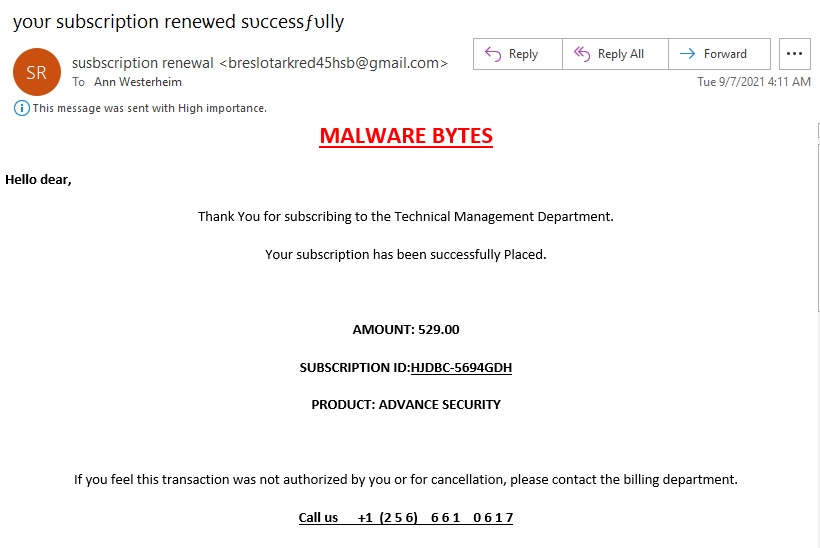
Cybersecurity Tip: Don't click on that link OR dial that number
Posted by Ann Westerheim on 9/7/21 2:57 PM
Perfect timing! Here's a phishing email that just arrived, and a prime example to show a few tips on how to spot a problem email. The subject of the email was "subscription renewal", and at the beginning of the month a lot of these may arrive in anyone's inbox. This one immediately caught my eye because the preview text showed "Hello dear". The other thing to note is that we've all been taught to not "click on the link", but this one invites us to call a number. That's a common new tactic and in the never ending cat and mouse game as computer users become more aware of dangerous links, the cyber criminals just come up with a new twist.
Read MoreTags: phishing, cybersecurity, cybersecurity training
.png)