Unless you're already using one of the new solid state hard drives, all of your critical business data is spinning around at 5400rpm or faster on a magnetic disk inside your computer. Think about it - it's a miracle any hard drive can actually work, and all your data is in a perilous situation! One of the most common system failures in a computer is a hard drive failure, but it doesn't have to be a disaster for you if you plan in advance.
Technology Advisor Blog
Ann Westerheim
Recent Posts
3 Things You Probably Didn't know about Microsoft Outlook Tasks
Posted by Ann Westerheim on 3/15/11 4:11 PM
At the beginning of the year, I made a New Years Resolution to get rid of all the paper on my desk. Two and a half months into the year, I'm proud to say I haven't had a single single post-it reminder on my desk in all this time! Where did all the post-its go? I eliminated all my paper reminders by finally getting serious about using Microsoft Outlook Tasks.
Tags: paperless, Microsoft Outlook tasks, productivity
One of the key technologies for your small business is a good document scanner. Getting all your paper into electronic format is big step for getting organized.
Tags: paperless, small business technology, scanner
Meaningful Use Requirements for Electronic Health Records
Posted by Ann Westerheim on 3/2/11 11:39 AM
As part of the American Recovery and Reinvestment act of 2009, the federal government has created substantial financial incentives for medical practices to implement Electronic Health Records (EHRs). The Medicare and Medicaid EHR incentive programs offer financial reimbursements to eligible professionals, hospitals, and critical access hospitals:
Tags: electronic health record, american recovery and reinvestment act
Is your password 123456? Time to increase your security!
Posted by Ann Westerheim on 2/17/11 9:00 AM
Well over a year ago there was a major security breach at a site called RockYou.com. One of the interesting outcomes is that the breach offered the opportunity to analyze password behaviors since over 32 million passwords were revealed.
Tags: Security, password, 123456, popular passwords
Here's a cool tech tool we recommend for saving time on your computer - Keybreeze. Keybreeze is basically a way to create short cuts to access files, applications, and web sites.
Tags: computer time saver, small business technology advice.
Join.me is a great new application from the folks at LogMeIn for screen sharing. If you're working on a project and you need to collaborate on a document, or if you want to do a presentation over the web, this is a VERY easy to use product. The free version has a lot of features and its probably all you need to get started.
Tags: join.me, Internet meeting, file sharing
Small Business Productivity/Security Recommendation - RoboForm
Posted by Ann Westerheim on 2/2/11 9:55 AM
With so many business and personal activities on-line these days, it's impossible to remember all the passwords. We've all been trained to use "strong" passwords (6 characters or more, not a word in the dictionary, numbers & symbols), but remembering them is a big problem.
Tags: Security, passwords, small business technology
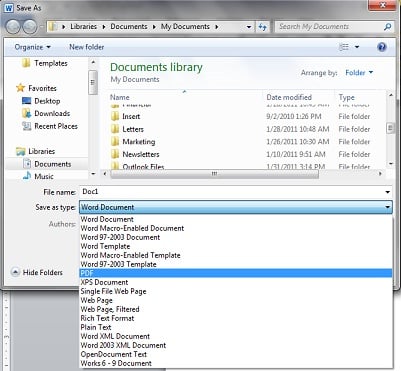
Here's a tip to get more from the small business technology you already have. One of the helpful features in Office 2010 is the ability to directly create a PDF document by using the "save as PDF" feature. Instead of relying on a third-party application, the capability is built right in.
Tags: PDF, small business, Microsoft Office, technology
Computer Security - Use "Sandboxie" to Surf the Web Safely
Posted by Ann Westerheim on 1/26/11 10:06 AM
The creators of viruses and other malicious software have gotten so aggressive recently, that today its possible to get a "drive-by" virus. You may be at a web site that seems safe, but if there are ads on the site, malicious code can enter your system just by viewing the ads. Unfortunately, the world of viruses is a "cat and mouse" game where the threats escalate as user protection increases.
Tags: computer security, Sandboxie, Sand Box
.png)