When it comes to establishing your business on a social media platform, a lot of teamwork and insight goes into its strategy. These calculations apply to tone, values, visuals, color, and messaging to find the right audience to interact with your content. What’s also important in maintaining social media is the security of general accounts and who monitors activity across these accounts. In the case of our social media presence at Ekaru, a small business MSP specializing in cybersecurity located within the outer metropolitan area of Boston serving small to medium sized clients. Our values are to be friendly, helpful, insightful, provide knowledgeable articles that align, bring up conversations surrounding awareness of good and bad cybersecurity practices to learn from. Along with cybersecurity practices to implement within your business, questions you may ask yourself are ‘how can I maintain a healthy social media presence that can apply for my business and self?
Read MoreTechnology Advisor Blog
Social Media Breaches Are on the Rise! How to Keep Your Accounts Safe
Posted by Sarah Carroll on 7/18/25 5:56 PM
Tags: small business, passwords, strong passwords, security protection, Monitoring, small business technology advice., cybersecurity, security awareness training, cybersecurity training, Cybersecurity, Social Media
Why Businesses Can’t Afford to Ignore the Summer Heat: Protect Your IT Assets from Overheating
Posted by Sarah Carroll on 7/11/25 9:56 AM
Temperatures are beginning to soar as the summer months roll in for businesses in Boston and all surrounding metropolitan areas. From laptops to tablets to servers, monitors, and portable hard drives, your business essential devices are vulnerable to the extreme heat if left unattended.
As your local Ekaru team, we want to help your business celebrate securely and ensure your IT systems stay protected while you enjoy some well-earned freedom.
Tags: Electronics overheating, lifecycle, small business technology advice., cybersecurity
Why Some Phishing eMails Still Get Through (Even with Good Security Filters)
Posted by Ann Westerheim on 7/10/25 10:02 AM
One of the questions we hear all the time is: “We have spam filters—so why are these phishing emails still getting through?” Sometimes, it’s said with a little more heat:
“Why don’t these security tools actually work?”
Tags: phishing, cybersecurity
Windows 11: Small Differences That Can Feel Big (and How to Navigate Them)
Posted by Ann Westerheim on 7/8/25 10:45 AM
Microsoft is ending support for Windows 10 on October 14, 2025 and the time to start planning is now. We work with a lot of local businesses in the Boston area, and one of the things we hear a lot is - later! It's always a little stressful to think about making a change, and when your "to do" list is long, this is easy to put on the back burner. Delaying your Windows 11 upgrade will only add risk and stress later, so get started now!
If you have a relatively new system, you probably won't need to purchase a new computer - you'll likely be able to just do a software update, which keeps costs a lot lower. When you're on Windows 11, you won't need another upgrade for many years (but security updates along the way are always important).
Read MoreWhy I Changed My Out of Office Auto-Reply - And Why You Should Too
Posted by Ann Westerheim on 7/3/25 10:06 AM
Are you sharing too much information in your Out of Office message? One of our core values at Ekaru is being "Friendly and Helpful". In that spirit, I used to include a lot of information in my Out of Office Auto-Reply... because I wanted to be friendly and helpful!
Read MoreTags: Cybersecurity, email scams, cybersecurity, Cybersecurity, Travel
What Is a Pen Test - and Why Small Businesses Can't Ignore It
Posted by Ann Westerheim on 6/27/25 4:08 PM
Penetration testing (or pen testing for short) is a proactive way to protect your business from cyberattacks. It simulates real-world attacks to identify vulnerabilities before cybercriminals can exploit them. For small businesses, often working with limited security resources, pen testing is a critical tool to uncover hidden risks, meet compliance requirements, and strengthen defenses.
Your business data and customer information need strong protection to maintain trust and meet compliance standards. Modern automated tools make professional security testing both accessible and cost-effective for smaller companies. Through regular testing, you can build a clear roadmap to strengthen your defenses and stay ahead of emerging threats.
Read MoreTags: security protection, business continuity, cybersecurity, data security, cybersecurity training, pen test, Penetration Testing
Cybersecurity Tips to Keep Your Devices Safe While Traveling This Summer
Posted by Sarah Carroll on 6/25/25 6:24 PM
It’s Summertime!!! You know what that means, our accumulated PTO is finally put to use to enjoy the outdoors and travel. For some, people travel is local, while others travel internationally for an adventure like no other. While traveling, your cellphone is your most prized possession, capturing memories, laughs and a focal point into monitoring your social media and other necessities.
Read MoreTags: Monitoring, cybersecurity, cybersecurity training, Cybersecurity, Travel
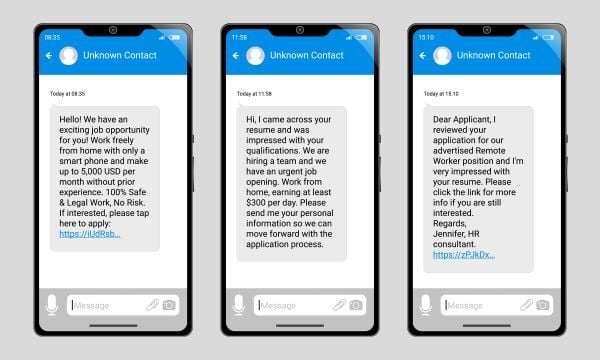
Although many of us have learned how to recognize scams, bad actors remain persistent and continue to send various fraudulent messages to our devices. Most of the time, they don’t care if the scam attempts are obvious or sophisticated, their main intention is to fatigue you to the point of becoming flustered and making a rushed decision to trick you. Some scams are isolated incidents, some are nationally present happening to your friends, family and coworkers.
Over the weekend, I received a text message on my personal cell phone from a ‘First Name-Last Name-###@RandomOrganization.org’.
The first thing I noticed right away was how detailed, long, and grammatically formatted the text was upon viewing. Usually, a lot of scam messages feel urgent. They’re trying to create an emotional response, utilizing that heightened state to influence victims to their CTA of malicious links. Mimicking an automated promotional SMS message businesses provide for their patrons that sign up to receive a discount. Seeing the message’s length, it is possible it can come off as legit before reading the contents within.
The second factor I noticed was the message coming from a random organization, stated within the message that they were from the Massachusetts Department of Motor Vehicles (DMV). These two did not match and that was my first indicator that this was a smishing attempt using the DMV to take aback trick anyone receiving the message. While I may have known the first indicators as someone new to cybersecurity but practices good cybersecurity hygiene, let’s continue the remaining text to dissect how to further identify this smishing attempt.
Tags: Monitoring, cybersecurity, cybersecurity training, Cybersecurity, Smishing
Cybersecurity Basics: What Is Multi-Factor Authentication and Why Does It Matter?
Posted by Sarah Carroll on 6/13/25 7:23 PM
Before social media and the responsibility of maintaining multiple accounts, folks tended to keep their passwords written down on paper, stored in what they considered a safe place, or saved into their phone. These are dangerous cybersecurity risks being practiced and they need to be addressed promptly.
The problem is passwords are often weak, reused or exposed in personal data breaches that are out of your control. In the last decade, we have been introduced to Password Managers and following right after, Multi-Factor Authentications (MFA). Both provide thorough measures to protect users’ information and safety. As an effect, this shield has caused bad actors to get creative and find other tactics to infiltrate your systems.
We’re going to go over what MFA is and why it matters to implement for your small business and in personal life or really, anywhere it’s available!
Tags: security protection, Monitoring, small business technology advice., cybersecurity, Privacy, security awareness training, cybersecurity training, managed IT services in Boston, Multi-Factor Authentication, MFA
How to Spot a Phishing Email: A Quick Guide for Small Business Teams
Posted by Sarah Carroll on 6/12/25 2:39 PM
Have you ever been hooked to a phishing attempt? Did you know that phishing is involved in 70% of breaches? Whether it’s an email, phone call, or text message, these are some of the common ways bad actors use to obtain your personal and financial information for malicious gain. Phishing emails were introduced into our lives decade(s) ago and have grown increasingly creative and sophisticated with native language use and perfect grammar.
Read MoreTags: small business, phishing, Cybersecurity, email scams, cybersecurity, ransomware, data security, spoofing, Security Awareness, email spoofing
.png)