The new Artificial Intelligence (AI) tool ChatGPT is all over the news these days! ChatGPT was created by OpenAI, and it's an AI language model that can understand human language and generate human-like responses. It's the fasted growing tech platform ever, hitting ONE MILLION users in just FIVE DAYS! You can ask a question and get a response. Need help writing an email or a letter to a client? You can automate a lot of repetitive tasks like writing an introductory email, an online ad, or even an outline of a book. It's a tool that can save you a lot of time when used right. If you have writer's block, or just can't think of how to start a response, just ask ChatGPT. The responses will require some fact checking and fine tuning, but you'll never have to stare at a blank sheet of paper again (a computer screen these days).
Read MoreTechnology Advisor Blog
ChatGPT Doesn't Keep Secrets - Create a ChatGPT Acceptable Use Policy to Protect Your Business
Posted by Ann Westerheim on 4/10/23 12:31 PM
Tags: small business, cybersecurity, Privacy, ChatGPT
Did you know? You can get call center technology on a small business budget
Posted by Ann Westerheim on 10/28/22 12:14 PM
At Ekaru, we've been partners with GoTo for several years now, and we've helped design, configure, install, and support phone systems for many local businesses in the greater Boston area. We've been using the system in our own office for several years, and the visual dial plan editor, the ability to work from everywhere, and integrated video conferencing are compelling features. Recently several of the local businesses we work with have taken the next step to implement "call center" features.
Read MoreTags: VoiP,, Phone System, SMB
Ekaru Announces Commitment to Growing Global Cybersecurity Success by Becoming a Cybersecurity Awareness Month 2022 Champion
Posted by Ann Westerheim on 9/28/22 5:35 PM
Building on annual success Cybersecurity Awareness Month 2022 is set to highlight the growing importance of cybersecurity in our daily lives and look to empower everyday individuals and business to take cybersecurity steps by making cyber more accessible.
Read MoreTags: small business, small business technology, cybersecurity, data security
I'm a Small Business. Why Would a Ransomware Gang be Out to Get Me?
Posted by Ann Westerheim on 9/20/22 11:38 AM
"I'm a small business. Why would a ransomware gang be out to get me?" This is a question we hear a lot working with local businesses. Everyone sees the big cyber crime headlines in the news, most recently with Uber, and last year quite visibly with the Colonial Pipeline, but what many people don't realize is that half of these kinds of threats hit small businesses - the events just don't make national news. Why are so many small businesses impacted when there are bigger targets out there? It's Ransomware as a Service. What's ransomware as a service? You’re likely familiar with software as a service (SaaS) but ransomware? What does that mean?
First, let’s do a quick review of what ransomware is. It's a type of malware that holds the victim’s files and folders for ransom. This sounds like something out of a Tom Cruise movie, but basically a giant warning shows up on your screen with a ticking clock that says pay the ransom, or you won't ever access your files again. Most typically, malware gets on your computer network through human error with someone inadvertently clicking on the wrong link or opening the wrong email attachment (like a fake resume). The malware is deployed and encrypts network data, with a safe return of your data being promised when the ransom is paid. And with payments usually made through cryptocurrency, these crimes are can be committed anonymously. Cybercrime is big business!
The "Ransomware as a Service" business model was developed for criminal purposes to make it even easier for criminals to conduct crimes. Ransomware requires little effort to deploy with potentially big payouts. Criminals with little or no technical know-how can now blast out millions of emails to potential victims. All they need is a few mouse clicks to make a lot of money.
Ransomware as a Service
Tags: small business, small business technology advice., cybersecurity, ransomware, cybersecurity training
These days, office phones are basically computers on your network. VoIP stands for "Voice over IP", which is a fancy way of saying that the phones work over a computer connection, not the old standard phone lines we all used to have. Years ago, if you had small business with about ten employees, you may have needed to get at least five phone lines to make sure that at least half of your team could be on the phones at the same time. If a sixth call came in, that would end up getting a busy signal. With VoIP, you can have as many simultaneous calls as you want, and it all works over your Internet connection - no "phone lines" needed.
Read MoreIT Industry Outlook 2022 - Getting back to Strategic Initiatives?
Posted by Ann Westerheim on 8/15/22 5:37 PM
We're more than half way through 2022, the world has been through a tough two years with the pandemic, and we're getting through to the other side. We just checked in again with the CompTIA IT Industry Outlook 2022 report, and it's pretty on track for the year. Ekaru is a proud member of CompTIA, and if you're not familiar with CompTIA, you should be! "The Computing Technology Industry Association (CompTIA) is the leading voice and advocate for the $5.3 trillion global information technology ecosystem. Through education, training, certifications, philanthropy, and market research, CompTIA is the hub for advancing the tech industry and its workforce."
Read MoreTags: small business technology, cybersecurity
Do your passwords pose a security risk for your business? At first this sounds like a funny question, because passwords are supposed to keep things secure, right? Well, not if they're recycled, weak, or not protected with multi-factor authentication! Your protection may not be as strong as you think, and getting better password practices is an important step in strengthening your cybersecurity. World Password Day was created by cybersecurity professionals in in 2013 and designated as the first Thursday of May. Now is a great time to help strengthen cybersecurity awareness in your team, and we've put together some resources for you to help to help foster better password practices.
Read MoreTags: small business, password, cybersecurity
Microsoft is introducing some pricing changes in March as part of their "New Commerce Experience" - or NCE. You may have seen this in the news as it has generated a lot of discussion, and you may be concerned about the impact the price increases and contract changes may have on you.
Read MoreTags: Microsoft 365, New Commerce Experience, Office 365
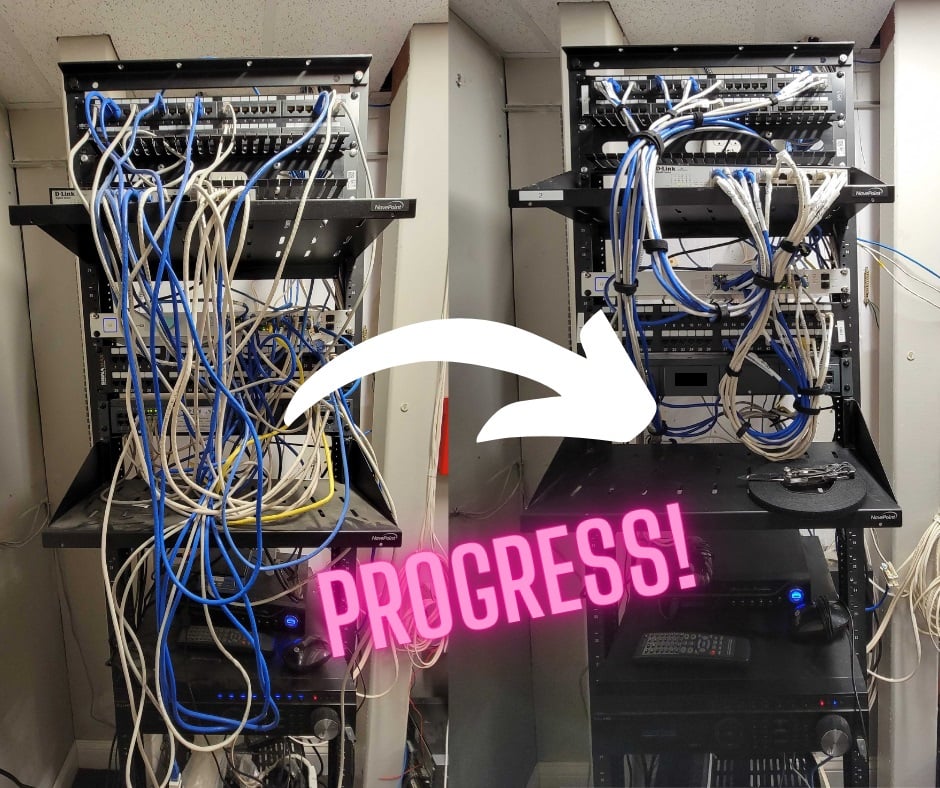
In the world of IT, things are happening all the time and it's easy to fall into reactive mode. Someone needs a password re-set, another person can't print, and someone else is having trouble with their webcam right before an important meeting. It can be hard to keep up, but stepping back and getting more organized will make a big difference. Often, keeping the network closet organized just falls of the list. Since no one really sees it, why does it matter?
Read MoreTags: small business technology, computer network
January is a great time to set some technology goals for your local business. So much technology is available to small businesses these days for digital enablement - work from anywhere, hybrid work, video, integration with Microsoft Teams... Things that only large enterprises could afford in the past are now available on a small business budget! If you haven't updated your tech in a while reach out to learn about what's new!
Read MoreTags: small business technology, VoiP,
.png)