Have you been in the middle of a significant deadline with complete focus, then all a sudden your desktop shuts down abruptly causing your focus and productivity to cease? It happens to the best of us.
Read MoreTechnology Advisor Blog
Shutdown vs. Restart: What’s the Difference and Why It Matters for Your Business
Posted by Sarah Carroll on 1/23/26 12:38 PM
Tags: Slow Computer, computer security, cybersecurity, Computer Tip, Computer Shutdown, Computer Restart
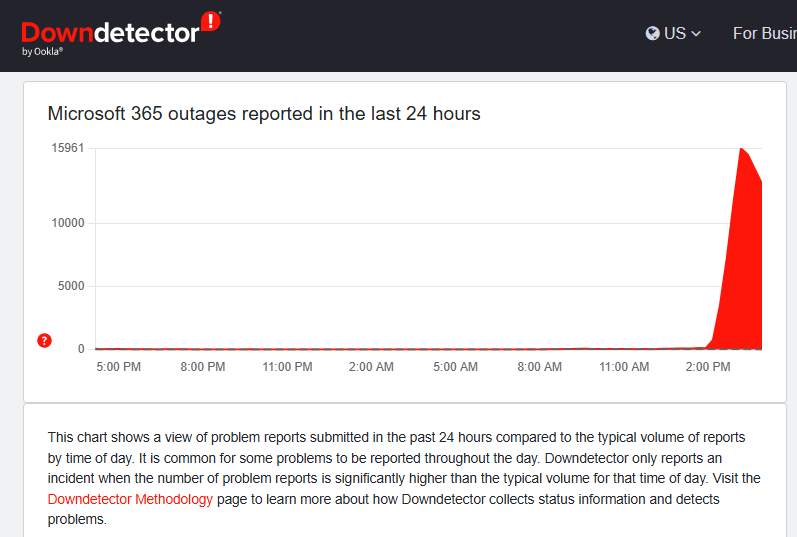
Microsoft 365 Outage Today: What's going on and why it matters
Posted by Ann Westerheim on 1/22/26 4:24 PM
Tags: Microsoft, Internet Outage, Microsoft 365
Why Rebooting Your Computer Is One of the Easiest Security Wins
Posted by Ann Westerheim on 1/21/26 5:42 PM
Security updates aren’t the most exciting topic—but they are one of the most important parts of keeping your business protected.
Right now, we’re seeing something that surprises a lot of people: about 13% of the systems in our community need a reboot. That means critical security updates are downloaded… but not fully protecting those computers yet.
Why reboots matter more than most people realize
Each month, Microsoft releases security fixes (often called “Patch Tuesday”). Behind the scenes, we carefully test critical patches within 24 hours, then roll out additional updates over the following week. This testing and deployment process is a core part of a healthy security program.
Here’s the catch: many of those security patches don’t actually take effect until you reboot. And we're seeing too many computers in our community that haven't been rebooted in too long.
Even more important, some patches are sequential. If the first update doesn’t fully install because the
Read MoreTags: Microsoft Security Patches, Patch Policy, cybersecurity
Before You Prove You’re Human, Make Sure You’re Not Helping Hackers
Posted by Ann Westerheim on 1/16/26 4:18 PM
Most of us barely notice CAPTCHA checks anymore.
You know the ones - the little box that says “I am not a robot”, or the quick image puzzle before you can move on. The little puzzle may ask you to select the images that contain traffic lights, bicycles, or crosswalks. We see them so often that clicking through has become second nature. In fact, many people associate CAPTCHAs with extra security, not risk.
Read MoreTags: cybersecurity, Cybersecurity Awareness Training
But wait - there's more! While we had a blog discussing Windows shortcuts to boost your productivity throughout the week, we also want to inform you of what’s to come for January 2026 updates regarding Windows 11. To provide an understanding of what’s coming your way, what you can expect for patch security updates, AI powered Copilot, PC features to devices, and more. Our intentions here at Ekaru are to provide our clients, and those searching for their next MSP, with the most up-to-date knowledge on all things cybersecurity and windows applications to ensure you are proactive and aware in the world of cybersecurity.
Read MoreTags: Security, Microsoft, Monitoring, cybersecurity, Windows11
Proceed with Caution: Post Holiday Surge in Phishing Campaigns
Posted by Sarah Carroll on 1/7/26 3:09 PM
Though it may be the beginning of a new year, the holiday remnants are evident when it comes to relentless cybercriminal activity. During the holidays, you had to be extra vigilant in managing your finances, buying gifts for friends/family, monitoring any unauthorized transactions, maintaining subscriptions, ensuring purchases came from legitimate websites and gift cards that were not tampered with. It’s understandable to feel fatigued in attempts to avoid being a potential target for cyber criminals. As hackers become more proficient with using AI tools and understanding your fears to enhance their phishing campaigns, the Ekaru team is here to help spread awareness of their evolving tactics, to prevent you from becoming their next victim.
Read MoreTags: Cybersecurity, email scams, cybersecurity, Text Scams, Fraud, Cybersecurity, Smishing, Identity Theft
As we move into 2026, we can reflect on the past year. 2025 has marked a significant shift with the integration of artificial intelligence into our workflows and daily lives. Whether welcomed or not, AI is now almost permanent part of the digital landscape, making it essential for organizations and individuals alike to stay informed and prepared, as cybercriminals seek to exploit these technologies for malicious intent.
Read MoreTags: cybersecurity, cybersecurity training, Artificial Intelligence, AI
The holidays are here, many larger companies have gone on company freeze, while many smaller businesses are beginning to close their devices to focus on family instead of work. During this time, it’s essential to ensure all safeguards are set up, that way cybercriminals don’t find an opportunity to cause havoc while you’re away. As your expert IT cybersecurity ally, we will discuss the steps you and your business should initiate in terms of updates, network safety, and phishing attempts before you clock out of the office.
Read MoreTags: security protection, Monitoring, security patches, small business technology, small business technology advice., cybersecurity, ransomware, cybersecurity, Cybersecurity, Travel, Cybersecurity, Social Media
8 weeks have passed since the highly anticipated sunset of Windows 10, leading to the transition of Windows 11 for most users. Throughout the last several weeks, many updates and security patches have been put in place to maintain high performance for users. As folks have updated their devices to Windows 11, a lot of users have experienced unusual glitches that Microsoft has resolved in real time. Let’s go over what updates have occurred so you are up to date and recognize anything you may have encountered within the last couple weeks!
Read MoreTags: Microsoft Windows Update, Microsoft, Microsoft Updates, cybersecurity, Windows11
Protect Your Workforce: Reducing Spam Calls Across Devices to Improve Productivity
Posted by Sarah Carroll on 12/15/25 12:39 PM
Let’s set the stage: It’s a Tuesday, still the beginning of your workweek and you notice 3 separate phone calls from an unknown number within the last 2 hours. For us in MA, these phone numbers commonly begin with (855), (866), (844) and sometimes even (774) which is a common area code in central MA. It seems like these spoofing spam calls are trying to reach you more than your friends and family. It’s distracting to receive these during the workday, and sometimes frustrating when trying to figure out the overall cause. You begin to block these unknown numbers, leading to even more calls causing you to wonder if your information has been leaked online somewhere. For iPhone, MAC, and Android users the uptick in spam calls is a nuisance.
Read MoreTags: spam filtering, spam, Wireless, cybersecurity, spoofing
.png)