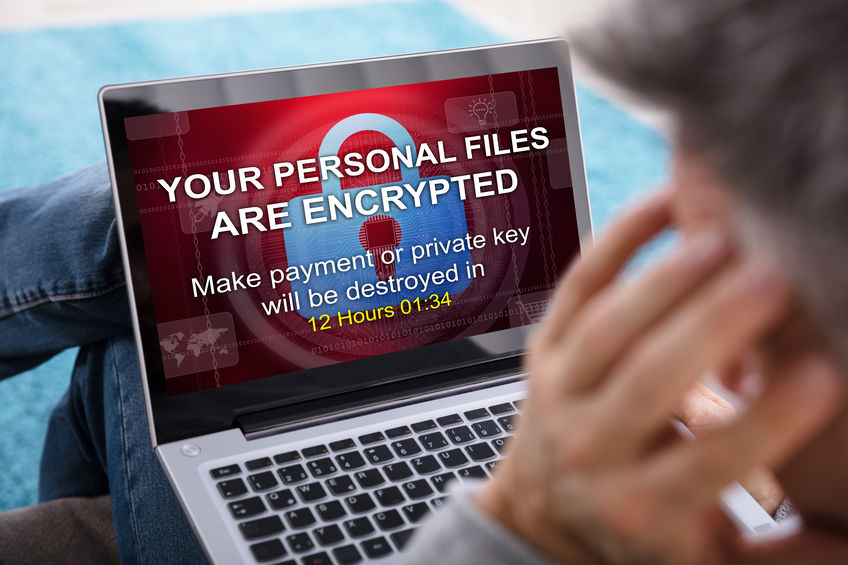
Ransomware threats are on the rise in recent years, and new threats are accelerating. This type of malware is extremely destructive as it encrypts the files of infected users and locks you out of your own data unless you pay the ransom, typically in the form of Bitcoin cryptocurrency, which enables criminals to hide. Its a big money maker for criminals, and as long as victims continue to pay the ransom, the threats will continue.
Read MoreTechnology Advisor Blog
Key Takeaways: Verizon Data Breach Investigations Report
Posted by Ann Westerheim on 7/29/19 5:07 PM
Each year Verizon publishes the much-anticipated Data Breach Investigations Report (DBIR). The report is built on real-world data from 41,686 security incidents and 2,013 data breaches provided by 73 data sources, both public and private entities, spanning 86 countries worldwide. We'll cover some of the key take-aways in this post, and if you're interested in more information, we recommend checking out the full report.
Read MoreTags: cybersecurity, ransomware
Professional Tax Preparers: Do you have a Written Data Security Plan?
Posted by Ann Westerheim on 7/25/19 9:01 AM
The IRS has issued a reminder to all practitioners that all "Professional Tax Preparers" must create a written data security plan to protect clients.
Read MoreTags: MA Data Security Law, cybersecurity, ransomware
Cybersecurity Awareness Training - Everyone Needs to Get Involved!
Posted by Ann Westerheim on 5/2/19 10:38 AM
Last week, Ekaru hosted a Cybersecurity Awareness Training session at the Cameron Senior Center in Westford, MA. It's part of our mission to raise cybersecurity awareness for EVERYONE.
Read MoreTags: cybersecurity, ransomware
Cyber Attacks Increasing - Cape Cod Community College Hacked for $800,000
Posted by Ann Westerheim on 12/12/18 12:01 PM
Cyber threats are real and they're local. Major corporations like Marriott make the big headlines, but too many smaller businesses and institutions think they're "under the radar". Attacks are widespread and they're automated. The average firewall is getting hundreds of thousands of intrusion attempts per month, over 50 ransomware attempts, and twelve phishing attempts. All it takes is ONE user clicking on ONE wrong link and a lot of damage can be done.
Read MoreTags: cybersecurity, SMB, ransomware
Disaster recovery is a basic element of good business continuity planning. You've probably heard the phrase and like many businesses, it's something you'll get around to "later".
Read MoreTags: backup, cybersecurity, ransomware
Tags: cybersecurity, ransomware
.png)