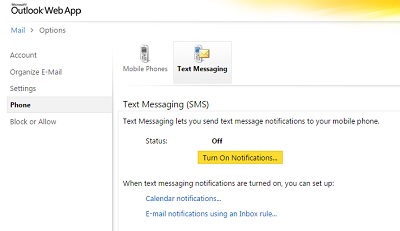
Have you ever been waiting for an important email and stuck filtering through your entire cluttered Inbox to check for it repeatedly until it arrives? With Ekaru cloud-based Exchange mail, you can set up a Text Message notification so you'll see when the important email arrives without needing to constantly check your Inbox.
Read MoreTechnology Advisor Blog
Wiring Closet / Network Gear: Are you a Felix or an Oscar?
Posted by Ann Westerheim on 2/9/15 12:43 PM
 It's that time of year - time for planning. You may have already completed your yearly plan in the Fall, but if you're like many small businesses, you're wearing many hats and even though January has passed, it's still planning season.
It's that time of year - time for planning. You may have already completed your yearly plan in the Fall, but if you're like many small businesses, you're wearing many hats and even though January has passed, it's still planning season.
The annual list of the worst passwords for 2014 has been posted. Last year, there were over three million leaked passwords. One of the interesting by-products of these leaks is the list of the top passwords. SplashData posted their list of the top-25 (and therefore, worst!) passwords. If you see any of your passwords on this list, change it!
Read MoreRecently one of our clients got a system infected with a virus and worried about whether or not they needed to report it. First, it IS possible to get a virus even though you're doing everything right, such as maintaining up-to-date anti virus protection, firewall protection, and security patch updates. But in most cases, although viruses can create a lot of damage and disruption, no data is exposed to the wrong hands.
Read MoreTags: Security Requirements, breach,
New Years Computer Security Resolution - Lock your Computer!
Posted by Ann Westerheim on 1/7/15 8:43 AM
With remote working and team collaboration now commonplace, employees demand anytime, anywhere access to their work files. When the workplace lacks these tools, employees take productivity into their own hands using their personal mobile devices and free or low cost consumer grade productivity apps to get stuff done. What they may not know is that these devices and consumer grade solutions typically lack the rigid security requirements that businesses demand and therefore are unintentionally introducing risk into the workplace. In order to minimize risk and maintain a secure environment, you need to standardize and develop use policies around data access. A good place to start is to standardize on your file sync and share solution. Let us help you make that transition easily and securely.
Read MoreThe Department of Homeland Security has issued an alert for Windows Server 2003 (TA14-310A). Microsoft is ending support for the Windows 2003 Operating System on July 14, 2015. After this time you will no longer receive security patch updates to protect against viruses, malware and other security threats. There will also no longer be any software updates or technical support available from Microsoft after this time.
Read MoreIs my UPS a Generator? Power Management for your Business
Posted by Ann Westerheim on 9/10/14 8:58 AM
Is my UPS a Generator? This might sound like a crazy question, and we're not talking about the delivery service with the brown trucks, we're talking about an Uninterruptible Power Supply (UPS). With last weekend's severe thunder storms in the area (and winter on the way), it's a good time to think about Power Management.
Tags: Power management, UPS, Surge protector
Security is the top technology concern among small business owners, and the flood of information about new security threats can seem overwhelming at times. Just about every week we see a new headline about a new threat or breach.
Tags: Microsoft Security Patches, Patch Policy, Compliance
.png)