8 weeks have passed since the highly anticipated sunset of Windows 10, leading to the transition of Windows 11 for most users. Throughout the last several weeks, many updates and security patches have been put in place to maintain high performance for users. As folks have updated their devices to Windows 11, a lot of users have experienced unusual glitches that Microsoft has resolved in real time. Let’s go over what updates have occurred so you are up to date and recognize anything you may have encountered within the last couple weeks!
Read MoreTechnology Advisor Blog
Tags: Microsoft Windows Update, Microsoft, Microsoft Updates, cybersecurity, Windows11
Protect Your Workforce: Reducing Spam Calls Across Devices to Improve Productivity
Posted by Sarah Carroll on 12/15/25 12:39 PM
Let’s set the stage: It’s a Tuesday, still the beginning of your workweek and you notice 3 separate phone calls from an unknown number within the last 2 hours. For us in MA, these phone numbers commonly begin with (855), (866), (844) and sometimes even (774) which is a common area code in central MA. It seems like these spoofing spam calls are trying to reach you more than your friends and family. It’s distracting to receive these during the workday, and sometimes frustrating when trying to figure out the overall cause. You begin to block these unknown numbers, leading to even more calls causing you to wonder if your information has been leaked online somewhere. For iPhone, MAC, and Android users the uptick in spam calls is a nuisance.
Read MoreTags: spam filtering, spam, Wireless, cybersecurity, spoofing
December is Here: Scammers Impersonating Products/Services Through Fraudulent Websites
Posted by Sarah Carroll on 12/2/25 3:11 PM
As Black Friday and Cyber Monday have come and gone; internet shoppers are facing a rise of fraudulent websites with counterfeit products, catered to their interests and demographic. These fraudulent websites are designed to steal innocent user’s credit card information along with their personal information. Causing additional stress on top of financial stress and holiday expectations. At Ekaru, we want to ensure you are safe this holiday season, and ensure your personal credentials are kept close.
Read MoreTags: Cybersecurity, email scams, cybersecurity, WebsiteScams, Fraud, Cybersecurity, Smishing, Cybersecurity, Social Media, Gift Card Scams
2025 Black Friday & Cyber Monday Scams To look Out For In Stores and In Your Inbox
Posted by Sarah Carroll on 11/25/25 4:58 PM
What's the difference between last minute shoppers and those not investing in cybersecurity for their small to medium sized businesses? Not very much! In both cases, impulsive decision making could potentially drain your finances and blow up in your face because you didn’t take the time to invest in safety protocols.
The holidays require a lot of time obtaining gifts for family and loved ones, and scammers are in the not-so-festive mood to try and drain your bank accounts. Black Friday is coming up with eye-catching sales, scammers are utilizing this time for all tactics to trick you into handing your personal information to them in the veil of receiving the ‘best sale of the year’.
Tags: phishing, Cybersecurity, email scams, cybersecurity, ransomware, Fraud, Cybersecurity, Social Media
Fake Flight Scam Texts & Identity Theft Targeting Holiday Travelers
Posted by Sarah Carroll on 11/21/25 11:01 AM
Between November and December, whether for work or the holidays, flights can be the most stressful part of anyone’s day when traveling. In most cases, arriving at the airport means keeping up to date with flight times, terminal changes, boarding times, checked luggage, TSA security, and arriving hours before your flight just to get through all checkpoints efficiently.
As stressful as it is, scammers are weaponizing the high emotional stress circling around flight schedules and doing the extra digging for your checked bag tags. Coming down the runway, travelers must be aware of fake airline texts, emphasizing cancelled flights and changes to be made expeditiously. With the world we live in, it’s best to keep your flight itinerary, luggage tags, and ticket information to yourself.
Tags: cybersecurity, Fraud, Cybersecurity, Travel, Cybersecurity, Social Media, Identity Theft
Gift Cards-An Easy Gift Solution but Proceed with Caution
Posted by Sarah Carroll on 11/13/25 10:40 AM
Coordinating a Wishlist for the holidays with your friends, family and loved ones can be challenging. Especially when no two people are the same. In a lot of cases, whether you utilize your time management right during the season or not, (it’s completely understandable if you don’t, it’s a stressful time in the work-life balance realm), sometimes the best gift, when you don’t know what to get, is a gift card.
Read MoreTags: phishing, email security, lifecycle, cybersecurity, Fraud, Cybersecurity Awareness Training, Gift Card Scams
In Ekaru’s previous blog, we went over how typos can unexpectedly lead you to mimicked websites designed by hackers to steal your personal information. But what if I told you that on top of having to be hyper vigilant of spelling, you also need to check a URL’s characters if all letters are from the same font?
Tricks hackers use to scam unsuspecting individuals usually consist of spam texts, phishing emails impersonating reputable companies, scams claiming you owe a specific amount of money, creating a sense of urgency - all are attempts to fatigue you and steal your information. For some, these tricks have become easy to spot due to recognizing the signs from their intensive cybersecurity awareness training. However, bad actors use evolving technology and strategies to improve their game and become harder and harder to detect.
One of their strategies to become harder to detect, is the usage of visuals in random letters from different fonts. This is a term we call Internalized Domain Name (IDN) Homograph attack.
Tags: phishing, Monitoring, technology, small business technology, small business technology advice., Cybersecurity, email scams, cybersecurity, DNS Protection, Homograph Attack
Typo Squatting: It'll Make Sure Think Twice About a Misspelled Website Domain
Posted by Sarah Carroll on 10/31/25 11:04 AM
As we enter Halloween, the larger national holidays such as Thanksgiving and Christmas are closing in. It’s a stressful time of year, causing a lot of folks to not act rationally how they usually would. Scammers are aware of this more than ever and will do whatever it takes for you to fall into their trap. How do they try to get you? Sometimes it’s not as obvious, sometimes its overlooking how a website HTTP link is typed out incorrectly. The term for this type of social engineering scam is called Typo squatting.
Read MoreTags: Cybersecurity, email scams, cybersecurity, Cybersecurity Awareness Training, Typo Squatting
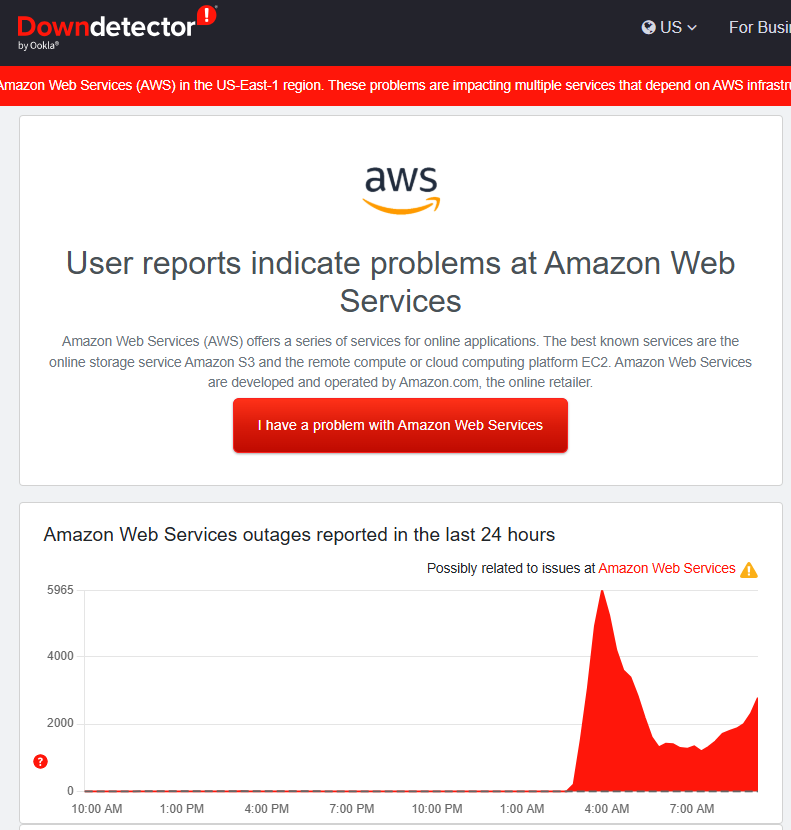
AWS Global Outage-The Importance of Backup Drives For Business & Personal Use
Posted by Sarah Carroll on 10/24/25 9:59 AM
As many of us have our head in the clouds for Halloween that is on a Friday this year, something spookier has grabbed folks’ attention this week. On Monday October 20th, people noticed that something was off. Social media apps taking minutes to send messages or to send at all, streaming shows not loading properly, difficulties in sending deposits through Venmo, or even grabbing a drink from Starbucks and their POS systems are down. The cause: AWS had an outage that lasted for over half a day on Monday (great way to start off the week amiright?) For many, frustration and eagerness took over as they could only wait for this to be resolved. But just how many internet services and applications were affected?
Read MoreTags: electronic documents, network security, cybersecurity, Internet Outage, google, AWS Outage, AWS
What Really Happens When Your Email Gets Hacked (And How to Stop It)
Posted by Ann Westerheim on 10/17/25 4:08 PM
This week, we received what looked like an official Request for Proposal (RFP) email from a local business we know. It was well-written, professional, and completely believable.
Read MoreTags: eMail, cybersecurity, hack
.png)