 In Ekaru’s previous blog, we went over how typos can unexpectedly lead you to mimicked websites designed by hackers to steal your personal information. But what if I told you that on top of having to be hyper vigilant of spelling, you also need to check a URL’s characters if all letters are from the same font?
In Ekaru’s previous blog, we went over how typos can unexpectedly lead you to mimicked websites designed by hackers to steal your personal information. But what if I told you that on top of having to be hyper vigilant of spelling, you also need to check a URL’s characters if all letters are from the same font?
Tricks hackers use to scam unsuspecting individuals usually consist of spam texts, phishing emails impersonating reputable companies, scams claiming you owe a specific amount of money, creating a sense of urgency - all are attempts to fatigue you and steal your information. For some, these tricks have become easy to spot due to recognizing the signs from their intensive cybersecurity awareness training. However, bad actors use evolving technology and strategies to improve their game and become harder and harder to detect.
One of their strategies to become harder to detect, is the usage of visuals in random letters from different fonts. This is a term we call Internalized Domain Name (IDN) Homograph attack.
What is a Homograph Attack?
A Homograph attack replaces characters with visually similar fonts from different alphabets. The font name in question is referred to as Cyrillic. Cyrillic is part of a Russian alphabet and in most cases, hackers will use vowels ‘a’ ‘I’ to impersonate the appearance of other letters from the Latin alphabet.
Hackers make fraudulent URLS look identical, making it almost impossible to tell them apart.
Compared to how typo squatting, where if you misspelled a URL in the search engine, the search engine brings you to a similar website identical to the one you are looking for mimicked by hackers. The real danger is if real users start going to the website under the impression it is still the correct one. In the case of a Homograph attack, the danger is right in the phishing email’s Hyperlink.
Look below of some examples of a Homograph attack. Some are far more challenging to identify than others.
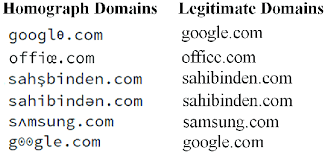

Facts Over Visual
Homograph attacks date far back to its first appearances in 2011. At first the scams website were used with silly intent, but within the last 14-15 years, hackers realized they can easily trick the human eye and hide a phishing scam in plain sight. With its malicious intents now, those reporting this new wave of phishing attacks noted the Cyrillic letter ‘a’ would be one of the indicators if the site was legitimate or malicious.
How to Combat Homograph Websites
Since homograph attacks have different character fonts hidden, there are some ways to identify without falling victim to their attempt.
- When a financial institution or any service you are expecting an interaction from, they will NOT reach out to you through phone call or text, UNLESS you specifically initiated to chat with their customer support.
- There are multiple types of scam dynamics in our present world today. A universal way to resolve cyber-attacks is through education. Cybersecurity awareness training. You can’t guard others and yourself if you don’t understand what you are dealing with.
How to Spot Cyrillic Font: - If you get an email phishing attempt but the link looks legit, but your gut feeling is off, try to copy and paste the URL onto a trusted browser instead of taking your chances by clicking on the link.
- Since browsers can limit what kinds of characters can be processed in a URL, if there are those characters present, the link will not function. This is one that will help quickly identify if it is a fraudulent URL based on the characters.
- In other instances, if you place the website name into a trusted URL, it will automatically correct to the legitimate URL and not the malicious one.
- If you’re feeling unsure, manually type the website/address name by hand or follow a trusted bookmark to desired website.
Ekaru’s Email and Website Filtering Systems
Cybercriminals are getting smarter every day, and small businesses are increasingly becoming their favorite targets. The best resource to combat these evolving scams is knowledge, proactive monitoring and engaging with a MSP that cares about you and your businesses needs. Here’s how we can help you stay protected:
Most attacks start with a phishing email, impersonating a trusted source leading to a fake website. Here's how Ekaru provides stronger email security;
- Email filtering to block suspicious senders and links.
- Anti-phishing policies that detect deceptive addresses.
- Authentication tools like SPF, DKIM, and DMARC to stop email spoofing.
These layers of protection make it much harder for fake messages to reach your team.
Watching Look-Alike DomainsLike typo squatting, attackers often purchase multiple fake domains that resemble business’s name or website.
- Monitor for similar domains that could be used in scams.
- Alert you when a suspicious look-alike site appears online.
Our cybersecurity training program can assist your team in detecting a scam and reacting proactively.
- To check links, hover over links before clicking.
- Recognize unusual or misspelled domain names before clicking on website in email.
- Report suspicious emails immediately.
To keep your team on your toes, we also provide phishing simulations to ensure your team is absorbing the material to keep themselves and their data safe.
Safe Browsing and DNS ProtectionEkaru’s services can protect your business at the network level by blocking harmful websites automatically.
Using tools like DNS filtering (for example, Zorus, Cisco Umbrella or Cloudflare Gateway), they can prevent your computers from even connecting to known malicious or fake domains. That means fewer chances for an accidental click to cause damage.
Endpoint and Firewall Defense- Endpoint detection and response (EDR) tools that stop suspicious activity fast.
- Firewalls and intrusion prevention systems that block malicious connections.
- Automatic software updates and security patches to close security gaps.
- Setting up a clear process for reporting phishing attempts.
- Providing 24/7 monitoring and rapid response to contain any breach.
- Helping your business recover quickly and minimize data loss.
- Setting cybersecurity policies for employees.
- Maintaining compliance with industry standards like ISO, NIST, or SOC 2.
- Offering regular reports and reviews to keep your defenses sharp.
By combining smart monitoring, strong security tools, and ongoing employee education, we can help keep your data, customers, and reputation safe.
If you’re ready to protect your small business from online threats, let’s connect! We have multiple plans that work alongside your budget and provide you with the sense of safety you need. 978-692-4200.
.png)