 Here's a re-cap of our recent community cybersecurity training event. Cybersecurity these days is like a game of chess. For every move, there's a counter move. As people put more technology protection in place, the cyber criminals just get more clever. User awareness is often the key to staying safe! Will your employee click on that dangerous link? It takes just one wrong click to do a lot of damage. The more you and your team know about the latest threats, the better. We were pleased to host close to 100 local small business leaders from Westford, Acton, Littleton, Chelmsford, Concord, Waltham, Southborough, Northborough, and Wellesley during our recent small business cybersecurity awareness training session. Education is a key part of Ekaru's mission, and here are a few highlights from the event.
Here's a re-cap of our recent community cybersecurity training event. Cybersecurity these days is like a game of chess. For every move, there's a counter move. As people put more technology protection in place, the cyber criminals just get more clever. User awareness is often the key to staying safe! Will your employee click on that dangerous link? It takes just one wrong click to do a lot of damage. The more you and your team know about the latest threats, the better. We were pleased to host close to 100 local small business leaders from Westford, Acton, Littleton, Chelmsford, Concord, Waltham, Southborough, Northborough, and Wellesley during our recent small business cybersecurity awareness training session. Education is a key part of Ekaru's mission, and here are a few highlights from the event.
One of the questions we here a lot is "Why do I need all this security stuff on my computer?" Which is often followed up with "If I have all this security stuff on my computer, why am I still at risk?" The short answer is that there's a lot of money in cyber crime.
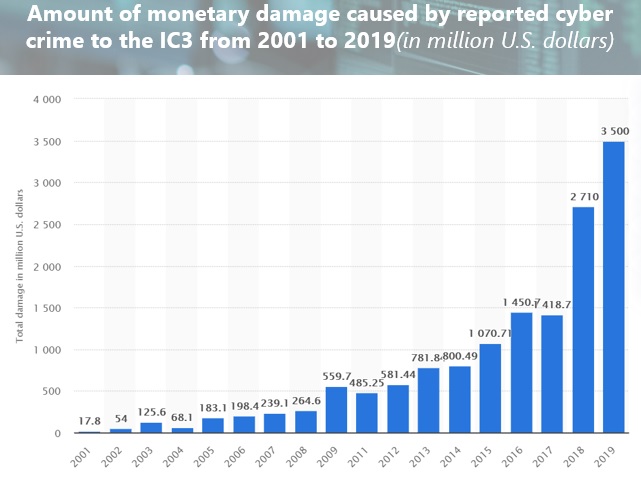
Here's the revenue growth reported over the last several years from the FBI Internet Crime Complaint Center (IC3). Cybercrime is a fast growing business - who wouldn't want a revenue growth curve that looks like that?!
A couple of other facts to keep in mind point to the need for ALL OF US to increase our cybersecurity knowledge.
- The FBI is currently getting 3000-4000 cyber complaints per day, up from 1000 per day before the pandemic.
- 85% of consumers won't do business with a company if they are concerned about its security practices
- 90% of breaches result from human error
- All businesses, regardless of size are at risk. Smaller businesses may feel like they aren't targets due to their size or their perception that their data isn't worth stealing (It's NOT about how important your data is to the criminals, its about how important is it to YOU - Could you run your business if you lost everything?
- The majority of attacks are indiscriminate. They target vulnerable computers regardless of where they reside (Fortune 500, small business, or home user.
Businesses can do a lot to help stay protected including security policies, technology protection, and employee education. Cyber awareness is a key part of staying safe, and the more you know about recent threats and scams, the less likely you are to fall for them.
Will you click on that link in your email inbox? Social engineering is at the heart of many types of scams. Here's a sample of a fake Amazon Order Confirmation email:
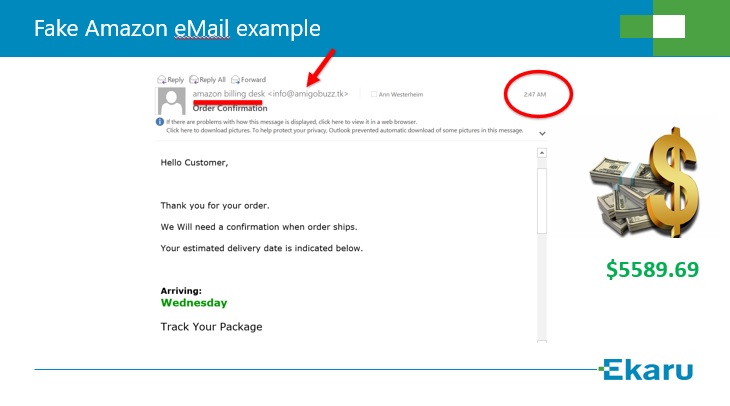
The "sender" is "amazon billing desk" but you can see in the fine print there's a completely different address listed (see the arrow). This email arrived at 2:47am which immediately seems out of the ordinary - but does it signal its a fake, or does it scare someone into thinking some hacker was in the account during the middle of the night. The size of the order is also quite large. Maybe one family member forwards the email to the other to say "What did you order???". The sender wants someone to click on the "track your package" link. These types of emails either try to harvest credentials by tricking your to log in, or deliver malware. You may think that you'd never get tricked like this, but when we run scheduled phishing tests on behalf of clients we ALWAYS see some links getting clicked.
During the training session we reviewed a lot of examples of Brand Impersonation, Phishing, FedEx scams, Microsoft scams, IRS scams, and more. The training session was recorded and can be viewed below.
Call us if you're interested in more cybersecurity training for your team!
.png)