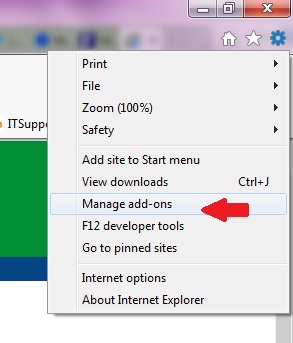
The latest security vulnerability is all over the news. Microsoft is working on a fix to address a flaw that could potentially allow hackers to gain remote access to systems. This flaw affects all versions of Intenet Explorer (about 55% of the browser market) and a patch is expected soon. If you're still running Windows XP, support has ended and there will not be a security patch.
Technology Advisor Blog
Latest Internet Explorer Security Threat - What you can do.
Posted by Ann Westerheim on 5/1/14 7:52 AM
Tags: Security, Internet Explorer, Adobe Flash
Cryptolocker may be lurking in that email - Don't open it!
Posted by Ann Westerheim on 2/3/14 5:12 PM
Many viruses are embedded in email attachments designed to get through even multiple layers of security. CryptoLocker is one of the worst viruses seen in years and it only takes ONE message to get through to cause a lot of damage, and the “bad guys” have developed sophisticated techniques to get around your antivirus protection.
Tags: Security, eMail, cryptolocker, antivirus
Did Santa bring you a new Kindle Fire, iPad Mini, or Microsoft Surface for Christmas? If so, probably one of the first things you wanted to do was connect to your home wireless network. To connect, you'll be asked for a "key", which is a code that lets you in (and keeps others out). The common dilemma is that users have set up a wireless network a LONG time ago, recorded the key, and stored it in a "safe place", only to be stumped when you look for it again. The problem is that after you program the key into your laptop or other portable devices, your system "remembers" it, so you end up forgetting.
Tags: Security, Encryption, Wireless Network, Key
February 7 is Safer Internet Day, which is organized by Insafe each year to help promote safer and more responsible use of the Internet and mobile phones, especially among young people. There are events all over the world today with this year's theme focused on "Connecting generations and educating each other". This is a great idea because we can all help each other - tech savvy young people can teach their grandparents about how to get around on-line, and grandparents have the wisdom to help their grandchildren stay safe.
Tags: Security, Internet, Safer Internet Day
One of the best ways to protect yourself from the common "fake" anti-virus malware that's all over the place is to spend a few moments getting to know your "real" anti-virus software.
Tags: Security, Fake Antivirus malware
Are "Default Passwords" our Defense Against Cyber-Terrorism?
Posted by Ann Westerheim on 11/23/11 9:07 AM
In last night's Republican debate, one of the questions posed to the candidates was "What threat might we face in the next few years that no one is talking about today?". The question was in the context of the 9/11 attacks shortly after George Bush became President, that defined his term in office. One of the answers that caught my attention was cyber-terrorism. Instead of a physical attack, our critical computer systems and networks could be attacked by hackers. When you stop and think about how pervasive computing is in our modern lives, covering everything from banking to delivery of our utilities, it's scary to think of how vulerable we are.
Tags: Security, passwords, strong passwords, default passwords
Just about every day we read about a new computer security breach in the news. The big events draw a lot of attention and generate the headlines, but small business owners need to stay vigilant too!
Tags: Security, Firewall, Virus, Spyware, Patches
Content Filtering - Get control over web usage in your business!
Posted by Ann Westerheim on 9/22/11 8:00 AM
One of the questions we're hearing more and more from our small business clients is how to get control over out-of-control web usage in the office. So much business is conducted on-line that employees need to be connected to the Internet, but in some cases, things can get out of control when some employees spend too much work time on personal web usage such as shopping, Facebook, or going to sites they're not supposed to. If web usage can't be controlled through other management techniques, or if your business has compliance requirements, it's time to think about content filtering for your site.
Tags: Security, network security, Internet usage, company policy
Free public Wi-Fi networks are popping up everywhere - at the airport, Starbucks, your local music school... These networks are a big convenience, but you should be aware of your security settings so you don't put your computer and data at risk. When you connect to a network, there may be a firewall protecting you from the outside world and everyone else on the Internet, but when you connect to a local network, you're basically putting your trust in that network and everyone else on it - not a good idea in public! In addition to file sharing, many of these wireless hot spots are unencrypted to make it easy for people to connect, but this could leave you vulnerable to malicious users in the coffee shop who could monitor your keystrokes!
Tags: Security, Encryption, Wi-Fi, Wireless
Is your password 123456? Time to increase your security!
Posted by Ann Westerheim on 2/17/11 9:00 AM
Well over a year ago there was a major security breach at a site called RockYou.com. One of the interesting outcomes is that the breach offered the opportunity to analyze password behaviors since over 32 million passwords were revealed.
Tags: Security, password, 123456, popular passwords
.png)