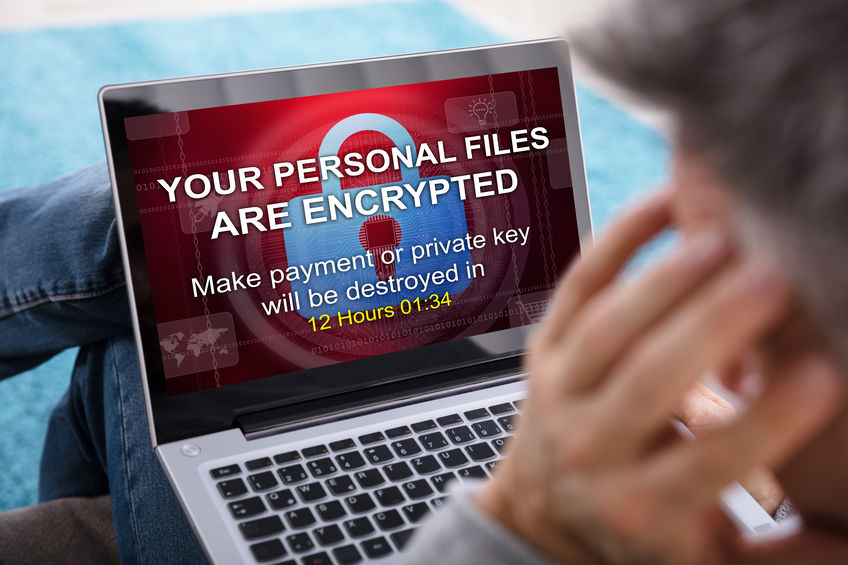
Ransomware threats are on the rise in recent years, and new threats are accelerating. This type of malware is extremely destructive as it encrypts the files of infected users and locks you out of your own data unless you pay the ransom, typically in the form of Bitcoin cryptocurrency, which enables criminals to hide. Its a big money maker for criminals, and as long as victims continue to pay the ransom, the threats will continue.
Read MoreTechnology Advisor Blog
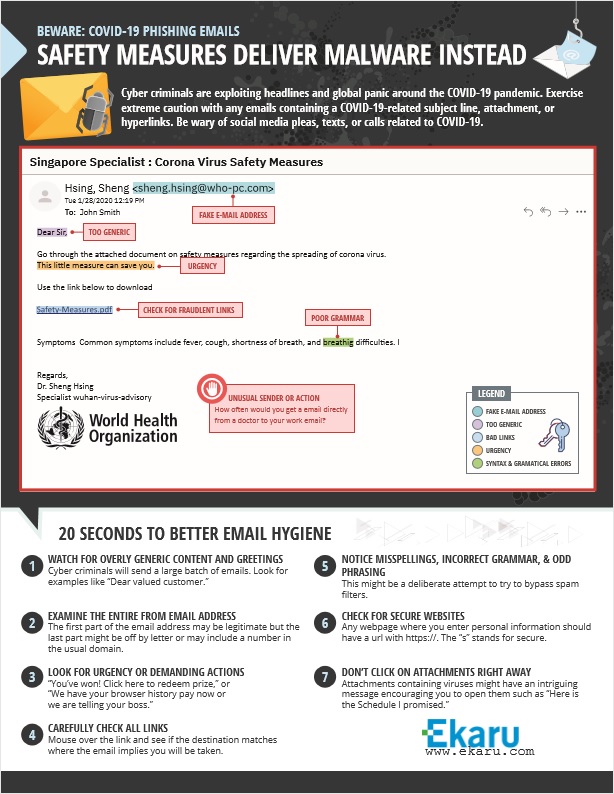
Cyber criminals are working overtime to take advantage of the disruption and confusion caused by the pandemic. The FBI reports a four fold increase in cyber threats recently and its more important than ever to stay alert, and talk to your team about cybersecurity. The most common attack vector these days is eMail, and an unknowing employee may click on the wrong link thinking they're getting important safety information. Think before you click!
Read MoreTags: Cybersecurity, email scams, cybersecurity, work from home
It's the holiday season and people are busy, and it's also a season to beware of scams. There are many different scams related to gift cards, and here's a new one we just saw locally.
Read MoreTags: Cybersecurity, email scams, cybersecurity
Cybersecurity is a LOCAL issue - Massachusetts school district pays $10,000 ransom to unlock its files after cyber attack.
Posted by Ann Westerheim on 5/2/18 3:59 PM
This past week a Massachusetts school district paid $10,000 ransom to unlock its files after a cyber attack. The Police Chief commented that there is no further investigation of this crime because solving this crime is "impossible". This is unfortunately a sign of the times.
Read MoreTags: Cybersecurity, email scams, cybersecurity, ransomware, cybersecurity
Train Your Workforce so They Don't Get Caught by a Phish!
Posted by Ann Westerheim on 8/2/17 11:21 AM
The US Department of Health and Human Services Office for Civil Rights July #Cybersecurity update reminds you to train your workforce so they don't get caught by a phish! This statement is specifically targeted to healthcare "covered entities" but really applies to all businesses and computer users.
Read MoreTags: Cybersecurity, email scams, training
Couple Lost Home over email Scam - What you need to know.
Posted by Ann Westerheim on 5/12/17 9:41 AM
Buying or selling a home can be a very stressful event, but with scammers on the sidelines, things can go to a whole new level. This past year, Jon and Dorothy Little were all set to close on their new $200,000 home in North Carolina when their Realtor sent an email to the closing attorney asking for wiring instructions to send money to the escrow account prior to closing. They received detailed instructions in reply, and promptly wired the funds. At the closing, they were shocked to find that the money was missing.
Read MoreTags: Cybersecurity, email scams
.png)