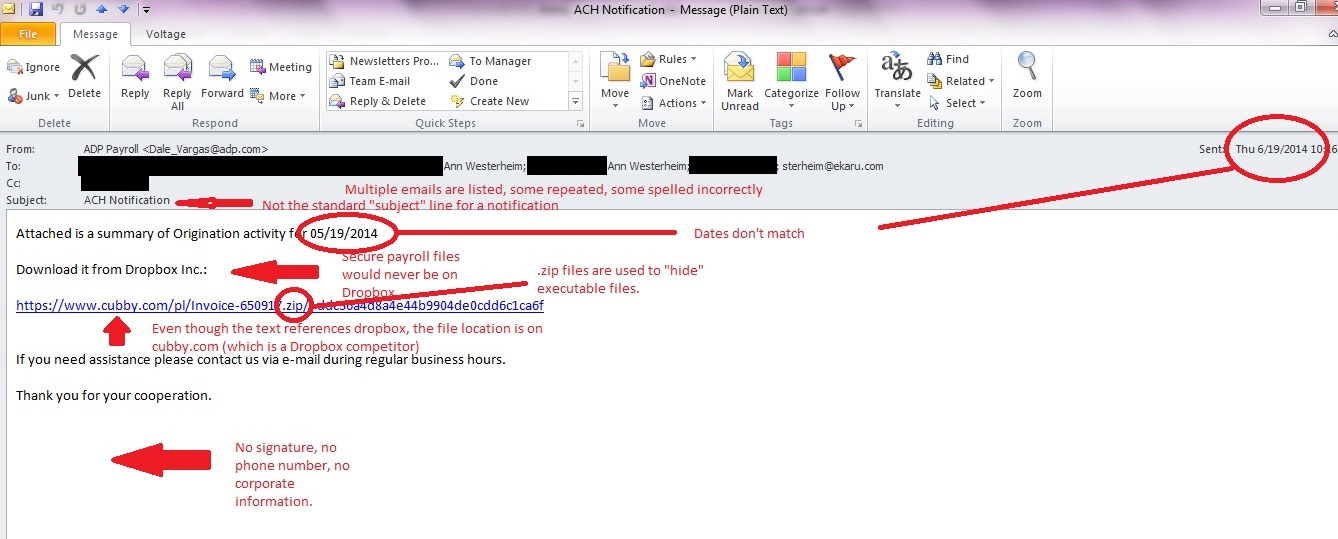
In our last post, we talked about suspicious emails that don't look so suspicious on the surface. Here is an example of an email to show you what to look for. In this case, a fake payroll report is being sent. A busy, distracted person may open this by mistake, or an opportunistic employee may try to open it to sneak a peek at confidential information. SLOW DOWN and check your mail carefully. Even with up to date antivirus protection and spam filtering, some emails CAN get through because they are engineered to get through. This can be a phishing email (trying to get confidential information) or a dangerous virus such as Cryptocker. Don't open the door!
Technology Advisor Blog
We've all heard that we shouldn't open suspicious emails. They can be phishing scams (attempts to get personal information such as username, password, and account number), or contain viruses. The problem is, the "bad guys" know we're on the lookout, and the real danger lies in emails that are disguised to not look suspicious.
Tags: Virus, eMail, cryptolocker
Just about every day we read about a new computer security breach in the news. The big events draw a lot of attention and generate the headlines, but small business owners need to stay vigilant too!
Tags: Security, Firewall, Virus, Spyware, Patches
.png)