If you want to zoom in or zoom out of a web page to make the font bigger or smaller, a simple trick is to use the control key and the scroll on on your mouse: Hold the control key (Ctrl) and then spin the scroll up or down. The scroll wheel is located between the left and right buttons on the mouse. Not every mouse has a scroll, so you can also use the control key with the plus sign and minus sign. A third option is to hit the ALT key plus "P" to pull up the page menu and then select "zoom".
Technology Advisor Blog
Tags: Internet Explorer, web page, font size
If you need to send an email to someone with a large file or perhaps with many smaller files, you can compress the files to save space and also save the hassle of attaching several files one by one by selecting a compressed folder. The process is easy, and it doesn't require any extra software since the function is built right into Windows. Simply find the file or folder you want to compress, right click on the file or folder and select Send To and then click Compressed (zipped) Folder. The new file folder has a zipper on it to show its "zipped", and you can rename it to anything you want.
Tags: eMail, Compress, Extract
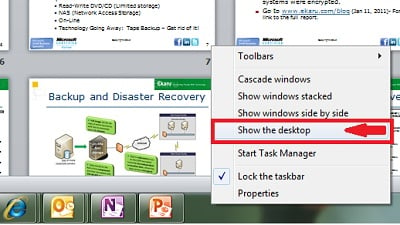
When I'm working on my computer I like to open up a LOT of windows at the same time. With so many windows open, if I need to go to the desktop to open a new program, there's a lot of clutter in the way.
Tags: Windows, short cut, Show the desktop
One of the best ways to protect yourself from the common "fake" anti-virus malware that's all over the place is to spend a few moments getting to know your "real" anti-virus software.
Tags: Security, Fake Antivirus malware
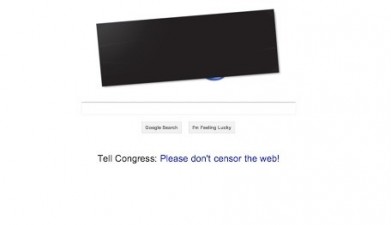
This week, Wikipedia went dark and Google blacked out its logo in protest over two controversial intellectual property bills being discussed in Congress: Stop Online Piracy Act (SOPA) and Protect IP Act (PIPA). The intent of the new laws is to protect authors and creators of intellectual property from getting ripped off. However both proposed laws are seriously flawed.
Tags: Internet, censorship, SOPA, PIPA
The Boston Sunday Globe had some interesting reading yesterday: "Laptop seizures at customs cause thorny legal dispute". When David House, a former MIT researcher, returned from vacation in Mexico a little over a year ago, federal agents seized his laptop at customs during a connection in Chicago, and kept it for almost two months. There was no search warrant, and he wasn't charged with a crime. The article describes a "Consitution-free zone" where governement agents don't need probable cause or reasonable suspicion to seize property, as long as it's not "invasive".
Tags: computer security, customs, seized laptop
.png)