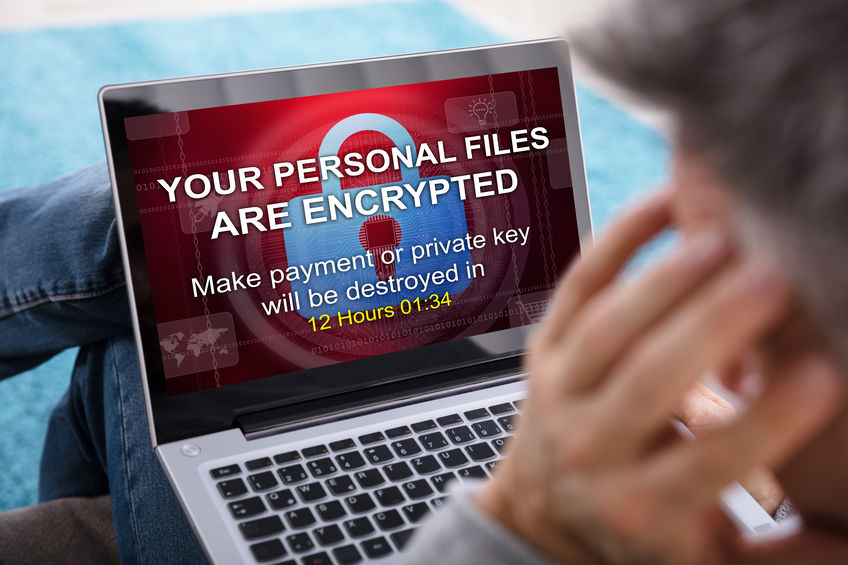
"I'm a small business. Why would a ransomware gang be out to get me?" This is a question we hear a lot working with local businesses. Everyone sees the big cyber crime headlines in the news, most recently with Uber, and last year quite visibly with the Colonial Pipeline, but what many people don't realize is that half of these kinds of threats hit small businesses - the events just don't make national news. Why are so many small businesses impacted when there are bigger targets out there? It's Ransomware as a Service. What's ransomware as a service? You’re likely familiar with software as a service (SaaS) but ransomware? What does that mean?
First, let’s do a quick review of what ransomware is. It's a type of malware that holds the victim’s files and folders for ransom. This sounds like something out of a Tom Cruise movie, but basically a giant warning shows up on your screen with a ticking clock that says pay the ransom, or you won't ever access your files again. Most typically, malware gets on your computer network through human error with someone inadvertently clicking on the wrong link or opening the wrong email attachment (like a fake resume). The malware is deployed and encrypts network data, with a safe return of your data being promised when the ransom is paid. And with payments usually made through cryptocurrency, these crimes are can be committed anonymously. Cybercrime is big business!
The "Ransomware as a Service" business model was developed for criminal purposes to make it even easier for criminals to conduct crimes. Ransomware requires little effort to deploy with potentially big payouts. Criminals with little or no technical know-how can now blast out millions of emails to potential victims. All they need is a few mouse clicks to make a lot of money.
Ransomware as a Service
Technology Advisor Blog
I'm a Small Business. Why Would a Ransomware Gang be Out to Get Me?
Posted by Ann Westerheim on 9/20/22 11:38 AM
Tags: small business, small business technology advice., cybersecurity, ransomware, cybersecurity training
Back to School: How to Get Started with an Employee Cybersecurity Training Program
Posted by Ann Westerheim on 9/8/21 4:38 PM
September is time for back to school and back to business! This is a great time to get serious about training your employees to understand their role in helping a business or organization stay safe.
Read MoreTags: cybersecurity, ransomware, cybersecurity training
When the pandemic hit, businesses all over the globe had to shift to remote work almost overnight. Now, with the vaccine rollout in full swing, the hybrid work model is gaining popularity. This allows employees to work from home, the office or split their time between both. According to a recent Accenture Report, close to 65% of businesses have adopted a hybrid model, and most workers prefer it that way.
However, a distributed workforce comes with its own set of challenges. One of the primary concerns of IT leaders across the globe is the unprecedented increase in cybercrime. The FBI reports that cybercrime has shot up by almost 300% since the start of the pandemic.
Relying on one basic security solution will, therefore, prove to be futile against sophisticated attack vectors. You may have seen advertisements on-line or on television promoting a single security solution that solves all your cybersecurity problems, but it just doesn't work like that! This is where an approach like Defense in Depth (DiD) finds its relevance. If you've attended any of our security workshops, we also often refer to this as "layers of security".
Defense in Depth is a cybersecurity approach in which multiple defensive methods are layered to protect a business. Since no individual security measure is guaranteed to endure every attack, combining several layers of security is more effective.
This layering approach was first conceived by the National Security Agency (NSA) and is inspired by a military tactic of the same name. In the military, layers of defense help buy time. But in IT, this approach is intended to prevent an incident altogether.
While Defense in Depth is critical to protecting your business against evolving cyberthreats, it’s an undertaking that requires time, extensive knowledge and experience. Partnering with a technology service provider like Ekaru can simplify the process, reduce stress and minimize opportunities for error.
How Your Small Business Can Help Defend Against Threats
All of the major cybersecurity protocols and frameworks (NIST, HIPAA, CMMC, etc) focus on three primary areas of control:
1. Administrative Controls
The policies and procedures of a business fall under administrative controls. These controls ensure that appropriate guidance is available and that security policies are followed.
Examples include hiring practices or employee onboarding and offboarding protocols, data processing and management procedures, information security policies, vendor risk management and third-party risk management frameworks, information risk management strategies, etc.
2. Technical Controls
Hardware or software intended to protect systems and resources fall under technical controls. Examples of technical controls are firewalls, configuration management, disk/data encryption, identity authentication (IAM), vulnerability scanners, patch management, virtual private networks (VPNs), intrusion detection systems (IDS), security awareness training, etc.
3. Physical Controls
Anything aimed at physically limiting or preventing access to IT systems falls under physical controls. Examples include fences, keycards/badges, CCTV systems, locker rooms, etc.
Essential Elements of Defense in Depth:
A technology service provider will help you implement all the elements of an effective Defense in Depth strategy to minimize the chances of threats seeping in through the cracks. These elements include:
1. Firewalls
A firewall is a security system comprised of hardware or software that can protect your network by filtering out unnecessary traffic and blocking unauthorized access to your data. We strongly advise implementing a "business class" firewall and not simply relying on what your Internet provider installed.
2. Intrusion Prevention and Detection Systems
Intrusion prevention and detection systems scan the network to look for anything out of place. If a threatening activity is detected, it will alert the stakeholders and block attacks.
3. Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions operate by constantly monitoring endpoints to find suspicious or malicious behavior in real time.
4. Network Segmentation
Once you divide your business’ network into smaller units, you can monitor data traffic between segments and safeguard segments from one another. If there's a breach in one segment of the network, the other segments may be protected.
5. The Principle of Least Privilege (PoLP)
The principle of least privilege (PoLP) is a cybersecurity concept in which a user is only granted the minimum levels of access/permissions essential to perform their task. If an employee doesn't need access to protected information, they should not have access. In many cases, over time data winds up being stored in a way that multiple people have access to it when they don't need to. Conduct regular audits of the data you hold.
6. Strong Passwords
Poor password hygiene, including the use of default passwords like “123456” or “admin,” can put your business at risk. Equally risky is the habit of using the same passwords for multiple accounts. To protect your accounts from being hacked, it’s essential to have strong passwords and an added layer of protection by using practices such as multifactor authentication (MFA).
Tags: cybersecurity, ransomware, cybersecurity, ransomware, cybersecurity training
Cryptocurrency is a term that we hear a lot, but for many of us, it remains a bit of a mystery. We’ll take a look at it from a high level to provide some understanding. Why? Well, it isn’t going away, and it only seems to be gaining popularity. And also, because if you are a target of a ransomware attack, it could very likely be how the hacker demands payment. Now, we are not suggesting you pay that ransom demand - in fact, the US Department of the Treasury has issued warnings against paying - but getting familiar with cryptocurrency will help you in understanding how these cybercriminals are able to fly under the radar.
Read MoreTags: cybersecurity, ransomware, cryptocurrency, bitcoin
It's Tax Season (with an extra month extension for COVID) which means its also the season for tax scams.
Read MoreTags: phishing, cybersecurity, ransomware
The FBI's Internet Crime Complaint Center (IC3) has just released its annual report. Over 700,000 complaints were filed - an increase of more than 300,000 from the previous year - and reported losses exceeded $4.2B.
Read MoreTags: small business, phishing, cybersecurity, ransomware
October was Cybersecurity Awareness Month, but Don't Stop!
Posted by Ann Westerheim on 11/12/20 10:43 AM
Each year the National Cyber Security Alliance promotes Cybersecurity Awareness Month during the Month of October. It's estimated that over 90% of breaches occur as the result of user error, so developing a culture of cybersecurity in your organization is more important than ever. Each day in October we posted a Myth or a Tip on our social media, and as much as a month of increased awareness helps, Cybersecurity is really an ongoing effort.
Read MoreTags: Compliance, cybersecurity, ransomware, security awareness training
Ransomware threats are on the rise in recent years, and new threats are accelerating. This type of malware is extremely destructive as it encrypts the files of infected users and locks you out of your own data unless you pay the ransom, typically in the form of Bitcoin cryptocurrency, which enables criminals to hide. Its a big money maker for criminals, and as long as victims continue to pay the ransom, the threats will continue.
Read MoreTags: Cybersecurity, email scams, ransomware
Key Takeaways: Verizon Data Breach Investigations Report
Posted by Ann Westerheim on 7/29/19 5:07 PM
Each year Verizon publishes the much-anticipated Data Breach Investigations Report (DBIR). The report is built on real-world data from 41,686 security incidents and 2,013 data breaches provided by 73 data sources, both public and private entities, spanning 86 countries worldwide. We'll cover some of the key take-aways in this post, and if you're interested in more information, we recommend checking out the full report.
Read MoreTags: cybersecurity, ransomware
Professional Tax Preparers: Do you have a Written Data Security Plan?
Posted by Ann Westerheim on 7/25/19 9:01 AM
The IRS has issued a reminder to all practitioners that all "Professional Tax Preparers" must create a written data security plan to protect clients.
Read MoreTags: MA Data Security Law, cybersecurity, ransomware
.png)