A few clients have asked us about recent notifications received from Network Solutions (and others): "Action Required: Notice Regarding Your Domain Name(s)". In this day and age, we recommend that all users stay alert when opening email, and we welcome questions about the legitimacy of received mail - better safe than sorry!
Read MoreTechnology Advisor Blog
Sending an email to more than just a few recipients? DON'T hit the send key before reading this....
Posted by Ann Westerheim on 4/16/18 3:54 PM
You need to send an important update or invitation to all your clients and you're ready to hit the "send" key. Don't!
Read MoreTags: eMail, email security
Modern technology enables us to accomplish so much, but when there's a disruption, we're reminded of our dependence, and it's painful! Last Thursday and Friday, many users were affected by delays in sending and receiving emails. The systems at Rackspace, one of the leading cloud providers in the world, became overloaded and disrupted services for many users, including a number of Ekaru clients.
Read MoreTags: eMail
Cybersecurity is a hot topic these days. We need "strong" passwords, we're not supposed to use the same pasword for multiple applications, and we need to change passwords on a regular basis. It's hard to remember all the passwords, and especially hard when you don't even know a password exists! Your email has a password, but its likely you don't remember it because you don't usually need it on a regular basis.
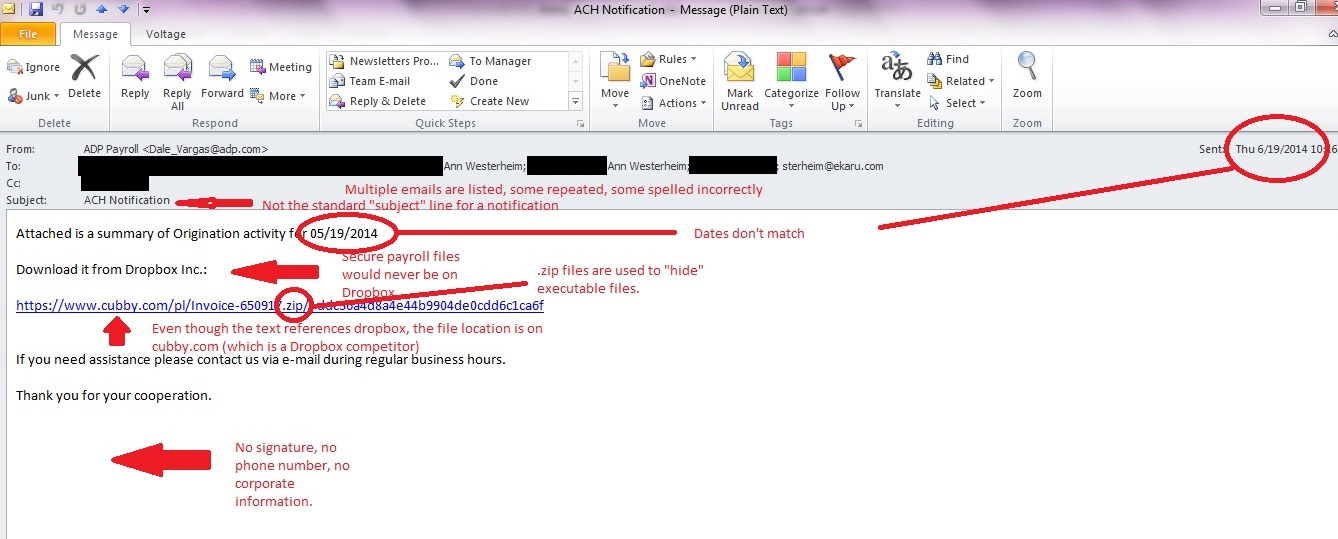
Read MoreIn our last post, we talked about suspicious emails that don't look so suspicious on the surface. Here is an example of an email to show you what to look for. In this case, a fake payroll report is being sent. A busy, distracted person may open this by mistake, or an opportunistic employee may try to open it to sneak a peek at confidential information. SLOW DOWN and check your mail carefully. Even with up to date antivirus protection and spam filtering, some emails CAN get through because they are engineered to get through. This can be a phishing email (trying to get confidential information) or a dangerous virus such as Cryptocker. Don't open the door!
Tags: Virus, eMail, cryptolocker, spam
We've all heard that we shouldn't open suspicious emails. They can be phishing scams (attempts to get personal information such as username, password, and account number), or contain viruses. The problem is, the "bad guys" know we're on the lookout, and the real danger lies in emails that are disguised to not look suspicious.
Tags: Virus, eMail, cryptolocker
Microsoft Outlook has a built in feature to process junk mail and send it to a "Junk" folder as a way to control Spam in your inbox. This is a great feature if you only read mail in one place, but for most users these days, mail is read on multiple platforms - smart phone, tablet, laptop, browser, etc. This is why we typically recommend filtering Spam in the "cloud" so the mail is filtered BEFORE it gets to your mailbox, and gets cleaned centrally before going to all your devices.
Tags: eMail, Microsoft Outlook, spam
We've recently started upgrading our Spam filtering platform, so it's time to post some updated instructions. These days Spam messages account for 80%-90% of all email sent worldwide, generating a lot of clutter and in some cases, security threats. We strongly advise filtering mail before it gets to your mail server, and many of our clients have signed up for Spam filtering services with us.
Tags: eMail, spam filtering, quarantine, Reflexion
At a recent industry event, I had the opportunity to share some "war stories" over lunch. One of the guys at the table told a tale of an email server crash on a Friday night that one of his techs rescued after many hours of effort late into the night. The Microsoft Exchange server had crashed, and they ran recovery and clean up tools to get the mail running again. Mission accomplished!
Tags: eMail, deleted items
Cryptolocker may be lurking in that email - Don't open it!
Posted by Ann Westerheim on 2/3/14 5:12 PM
Many viruses are embedded in email attachments designed to get through even multiple layers of security. CryptoLocker is one of the worst viruses seen in years and it only takes ONE message to get through to cause a lot of damage, and the “bad guys” have developed sophisticated techniques to get around your antivirus protection.
Tags: Security, eMail, cryptolocker, antivirus
.png)