It's the holiday season and people are busy, and it's also a season to beware of scams. There are many different scams related to gift cards, and here's a new one we just saw locally.
Read MoreTechnology Advisor Blog
A Creepy eMail in Your Inbox - Someone Knows Your Password
Posted by Ann Westerheim on 11/12/18 10:02 AM
The Cybersecurity landscape is constantly changing, and there's a new threat to watch out for: Extortion emails that contain either a past or current password. We saw a big wave of these emails over the summer and shared a blog post with our community,: A Creepy Twist on Ransomware: Using your Hacked Passwords and we're seeing another wave now, with some more variations.
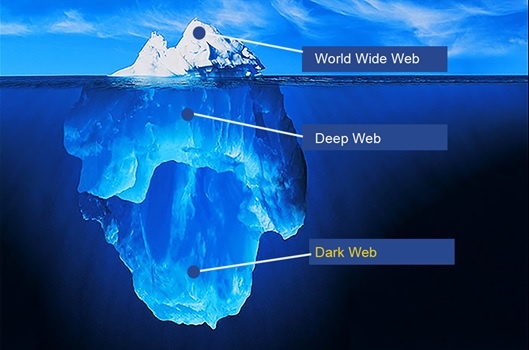
Read MoreIdentity theft is an unfortunate occurrence that is all too familiar with most business owners, but do those individuals know where the compromised data will end up? Often, these business owners are unaware of the virtual marketplace where stolen data is purchased and sold by cybercriminals; a place known as the “Dark Web”.
Read MoreTags: cybersecurity, Dark Web
The "tech support" scam is a common threat on the Internet. While working on your computer, a pop up will appear that says your computer has a problem and help is just a phone call or click away. Many of these scams pretend to be from Microsoft. The graphics may look very professional, and the tech jargon sounds convincing enough that may people fall for these scams. After the "repair" is done, then you'll be asked for a credit card to pay. Most people assume they won't fall for a scam, but if you're very busy, and the support price is low enough, it could seem like the fastest and most efficient way to get support and get back to work.
Read MoreTags: cybersecurity, data security
.png)