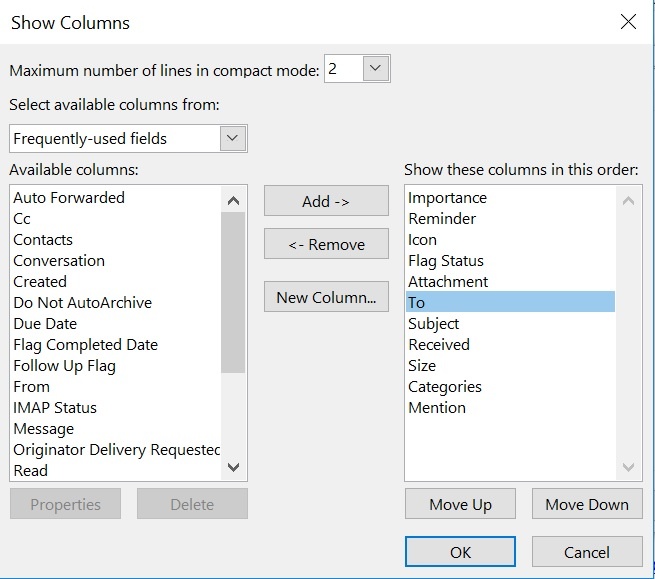
We hope you're keeping up with organizing your "Inbox" in Outlook using different folders to group your mail. You may also want to organize your "Sent Items" folder into different sub-folders. Perhaps you have some company related emails you want to group or perhaps you want to track your sent items by major projects. If you add a sub-folder, you may be alarmed to see that all the mail is listed with your name. As you can see below, my messages in my newly created "TEST FOLDER" folder for sent messages are all listed by who sent the message. Me! Not helpful. I already know who sent them!
Read MoreTechnology Advisor Blog
Tags: Microsoft Outlook
Facebook Privacy - Big Brother is watching you and has been for a long time!
Posted by Ann Westerheim on 3/22/18 1:44 PM
Facebook is in the news recently for some not so good reasons. In case you missed it, a research firm called Cambridge Analytica harvested the personal information of 50 million Facebook users, and used this to "influence" the Presidential election. After days of silence, Facebook executives have finally come forward and would like users to think that this was an isolated case by some bad actors, but the real problem here is that this actually hits at the core of the Facebook business model.
Read MoreTags: cybersecurity
Phishing: Would your employees click on any of these emails?
Posted by Ann Westerheim on 3/15/18 2:02 PM
Everyone thinks they won't click on a phishing link, but when we run tests, there's always someone who does!
Read MoreTags: Microsoft Security Patches, cybersecurity, ransomware, training, HIPAA
At the HIMSS Healthcare IT Conference last week in Las Vegas, Roger Severino, Director of the US Department of Health and Human Services Office for Civil Rights (OCR), the HIPAA enforcement agency, made some news when he said that health care providers may share Protected Health Information (PHI) with patients through standard text messages. Providers must first warn their patients that texting is not secure, gain the patients’ authorization, and document the patients’ consent. Note that this only applies to communications with patients.
Read MoreTags: Compliance, cybersecurity, data security, HIPAA
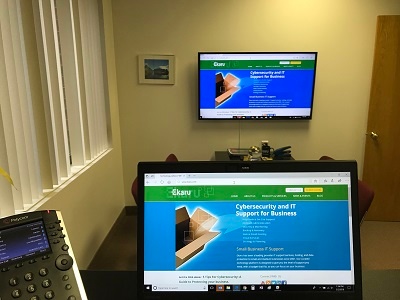
Technology, Patience, and Wireless Displays... Lesson Learned.
Posted by Ann Westerheim on 3/2/18 2:15 PM
I love technology! It's amazing that I can project the screen of my laptop across the room to a large TV ... through the air! No cables or connections needed. Wow!
Read MoreTags: Microsoft Display Adapter
.png)