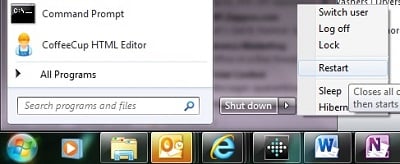
Every day we review security patch compliance for all our clients with managed services coverage with us. Often, we see systems with security patches pending reboots. Many security patches require a reboot to install, and some security patches are sequential, so the next one won't install before the previous patch is complete. This can result in a system that isn't fully protected.
Technology Advisor Blog
Tags: Reboot, security patches
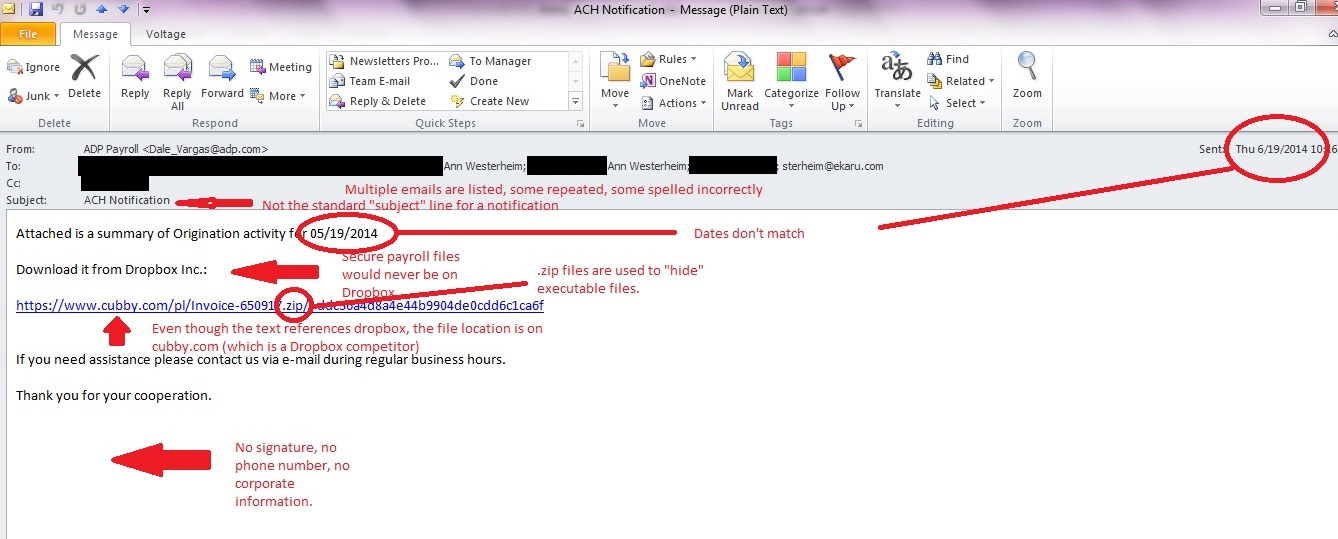
In our last post, we talked about suspicious emails that don't look so suspicious on the surface. Here is an example of an email to show you what to look for. In this case, a fake payroll report is being sent. A busy, distracted person may open this by mistake, or an opportunistic employee may try to open it to sneak a peek at confidential information. SLOW DOWN and check your mail carefully. Even with up to date antivirus protection and spam filtering, some emails CAN get through because they are engineered to get through. This can be a phishing email (trying to get confidential information) or a dangerous virus such as Cryptocker. Don't open the door!
Tags: Virus, eMail, cryptolocker, spam
We've all heard that we shouldn't open suspicious emails. They can be phishing scams (attempts to get personal information such as username, password, and account number), or contain viruses. The problem is, the "bad guys" know we're on the lookout, and the real danger lies in emails that are disguised to not look suspicious.
Tags: Virus, eMail, cryptolocker
Removing entries from your Outlook email "nickname" cache
Posted by Ann Westerheim on 6/5/14 9:29 AM
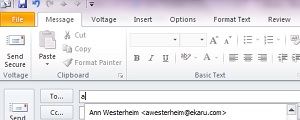
Outlook has a time saving "autocomplete" feature that's a big help most of the time, but can sometimes cause issues. When you compose a new email message in Outlook, as you start to type in the first few letters of the recipient's email address, you'll see that Outlook will have suggestions for you based on who you have emailed before. This is a great time saver, and over time your list will grow. An important thing to know, is that it's not actually your address book, it's a cached list of anyone you have emailed in the past.
Tags: Outlook, autocomplete, nickname, .nk2
.png)