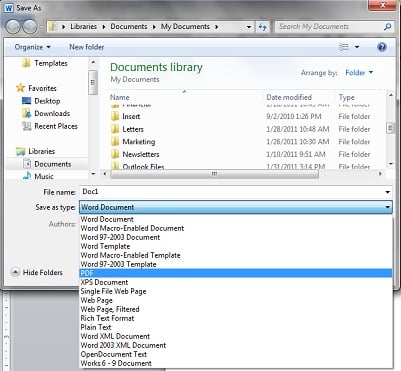
Here's a tip to get more from the small business technology you already have. One of the helpful features in Office 2010 is the ability to directly create a PDF document by using the "save as PDF" feature. Instead of relying on a third-party application, the capability is built right in.
Technology Advisor Blog
Tags: PDF, small business, Microsoft Office, technology
Computer Security - Use "Sandboxie" to Surf the Web Safely
Posted by Ann Westerheim on 1/26/11 10:06 AM
The creators of viruses and other malicious software have gotten so aggressive recently, that today its possible to get a "drive-by" virus. You may be at a web site that seems safe, but if there are ads on the site, malicious code can enter your system just by viewing the ads. Unfortunately, the world of viruses is a "cat and mouse" game where the threats escalate as user protection increases.
Tags: computer security, Sandboxie, Sand Box
In this day and age of all sorts of computer viruses and threats, a big problem for businesses is what to do with systems used by multiple people.
Tags: laptop, small business, computer, security protection
A customer contacted us a few days ago with an email dilemma. They had been receiving a valued daily report through email, and all of a sudden they stopped receiving it and found that it was in their spam filter and wondered why.
Tags: small business, eMail, spam
Laptop Encryption - Part 2 - Know the Difference Between "Sleep" and "Hibernation"
Posted by Ann Westerheim on 1/11/11 9:28 AM
Good news, you've protected your laptop (and your business and your customers) by encrypting it. Now, now an encryption key will be needed to access confidential or protected information.
Tags: laptop, Encryption
The Billion Dollar Lost-Laptop Study - Protect your Small Business!
Posted by Ann Westerheim on 1/11/11 9:27 AM
The "Billion Dollar Lost-Laptop Study" conducted by Intel and the Ponemon institute, reports that more than 300 businesses lost more than 86,000 businesses last year worth a staggering $2.1B.
Tags: computer security, Encryption, laptop loss
Going Paperless for our Small Business - The next step - shredding!
Posted by Ann Westerheim on 1/6/11 9:54 AM
With our file cabinets so full we could barely squeeze in another piece of paper, it was time to shred! Our process is already in place going forward to keep paper away, but there still was the 800-lb gorilla of the full file cabinet to deal with.
.png)